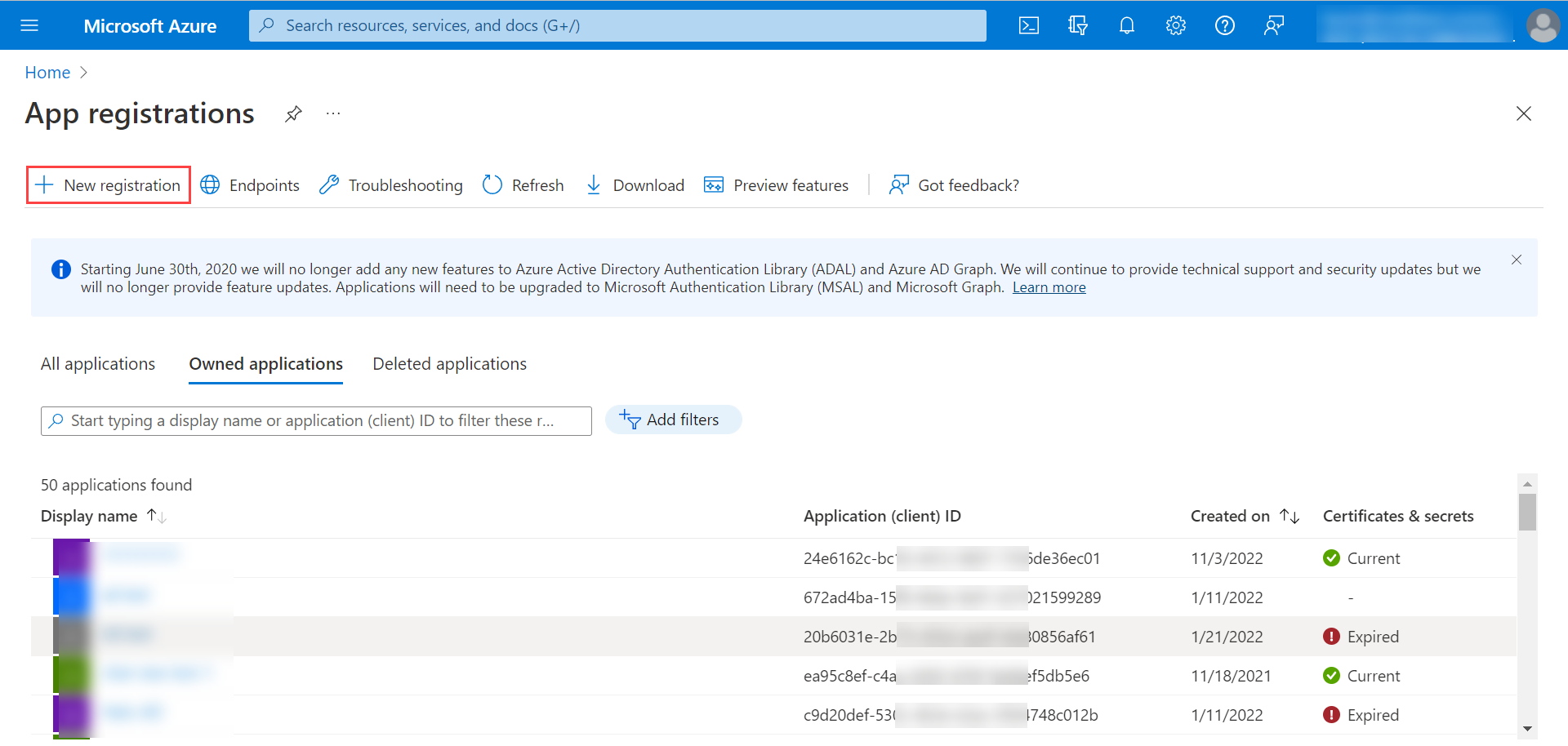
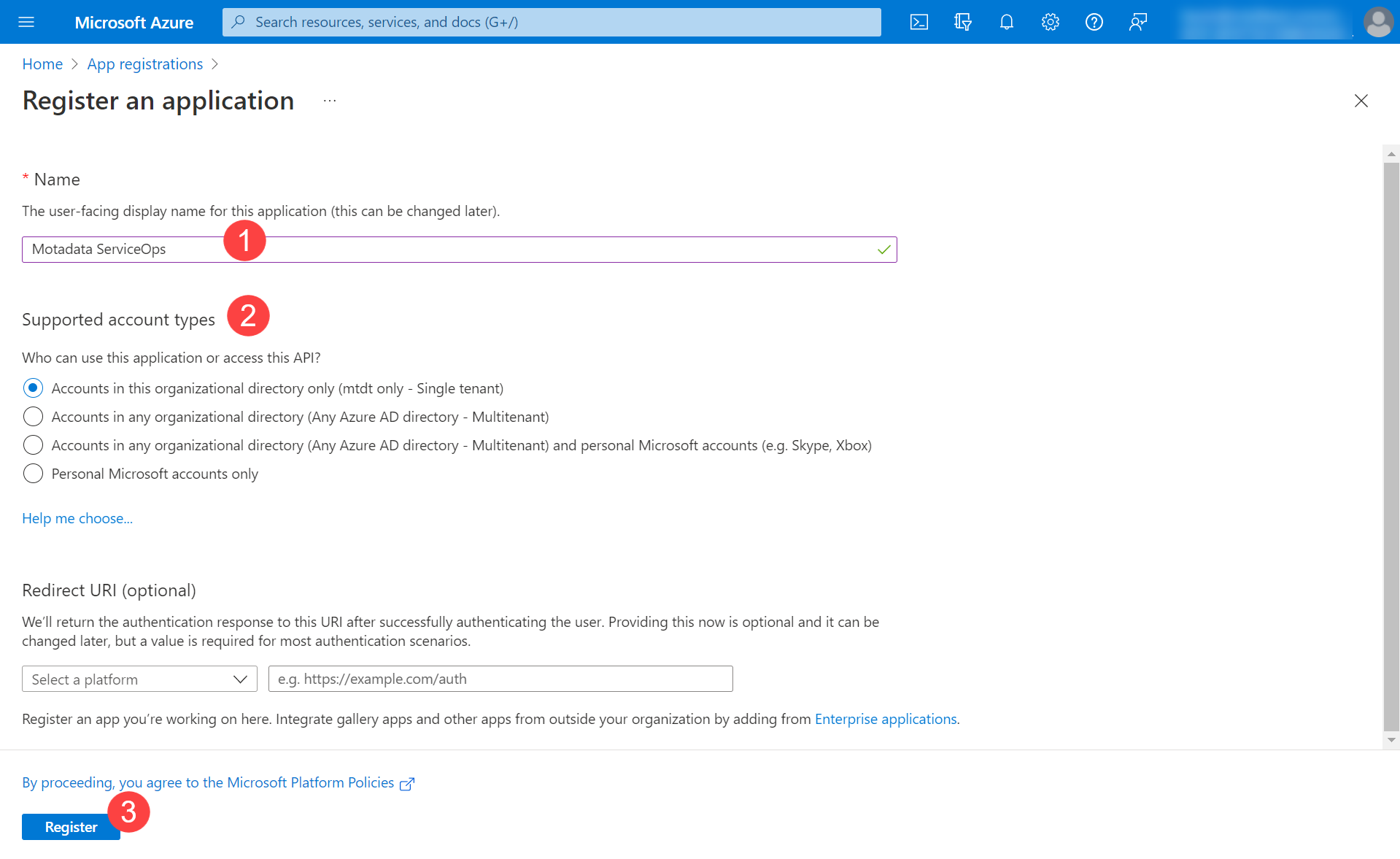
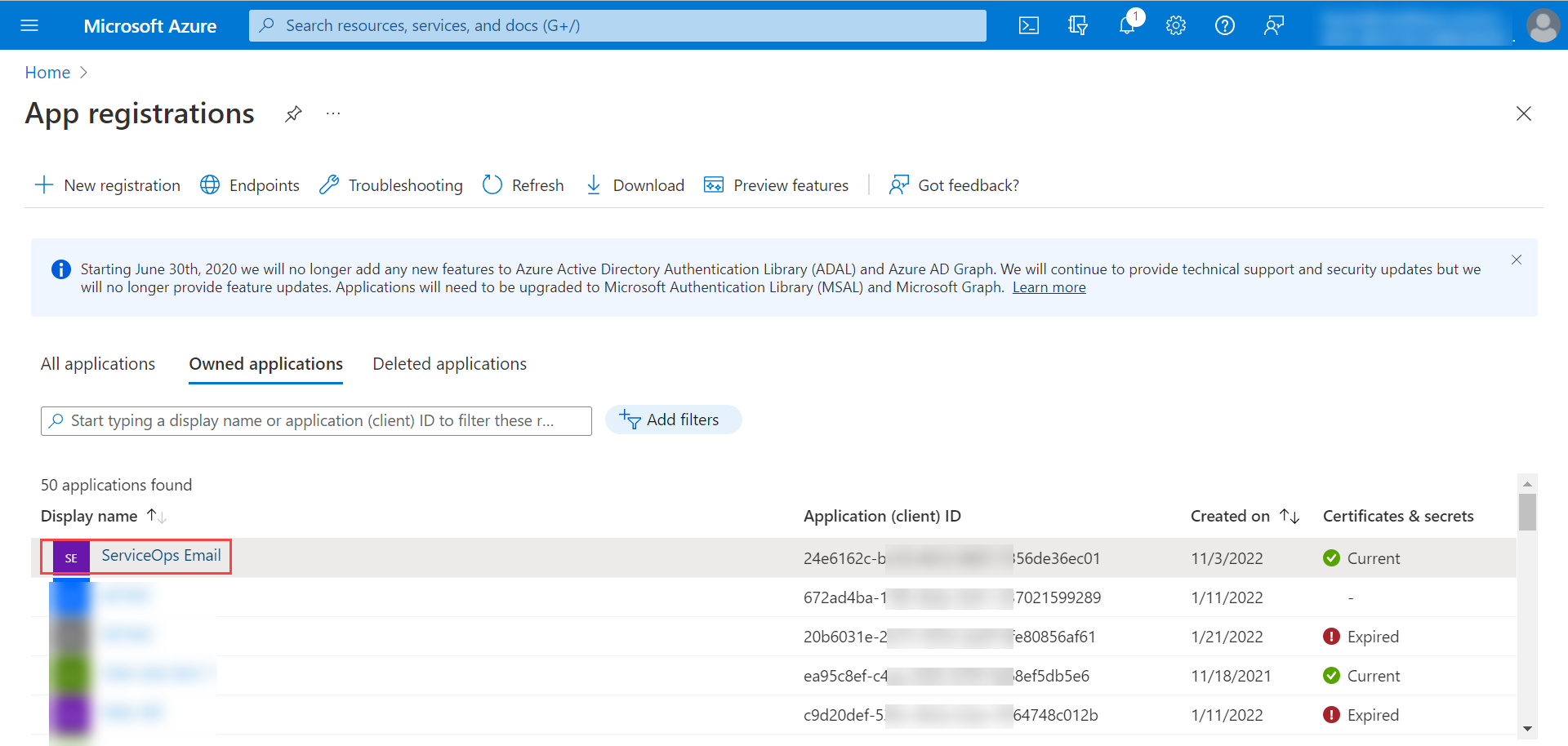
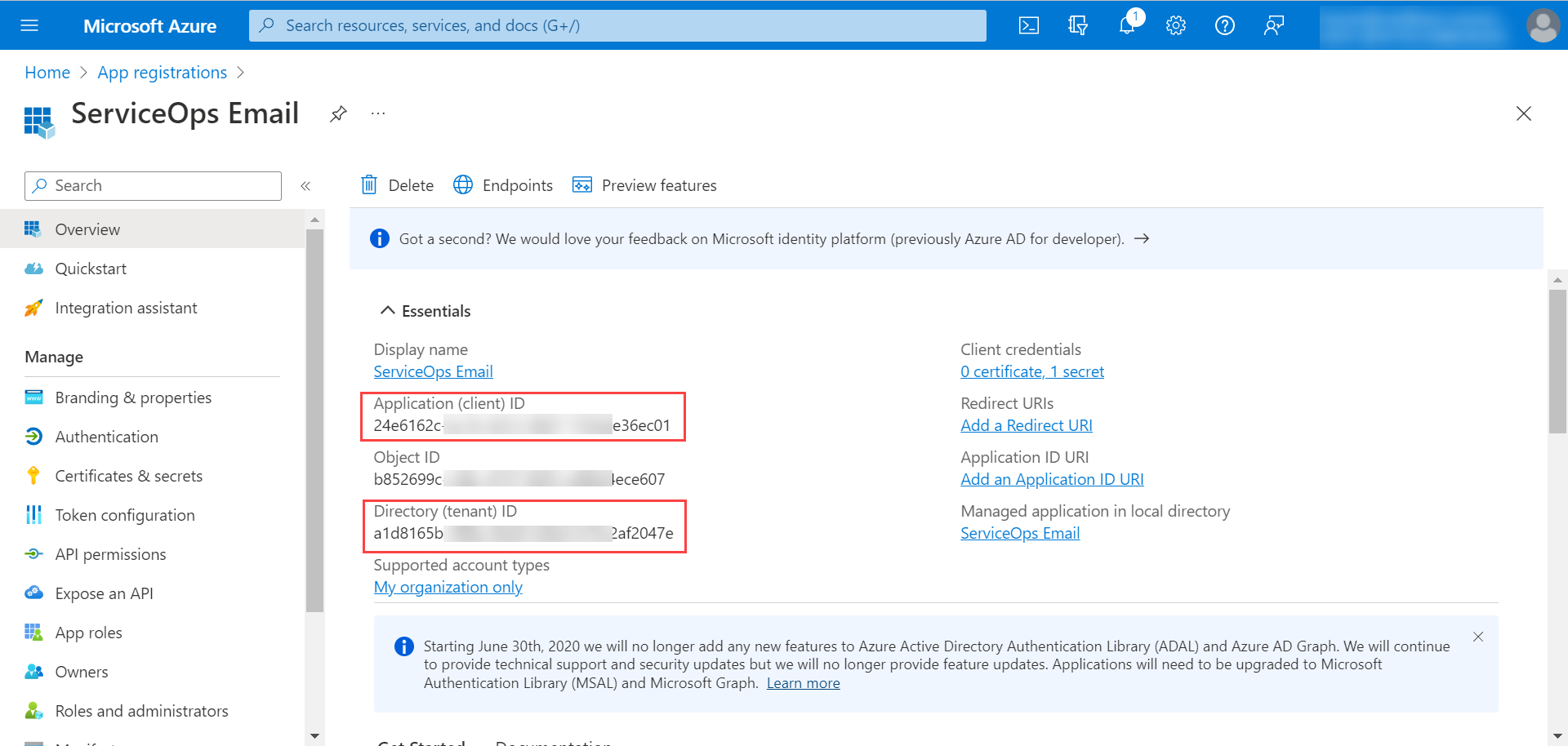
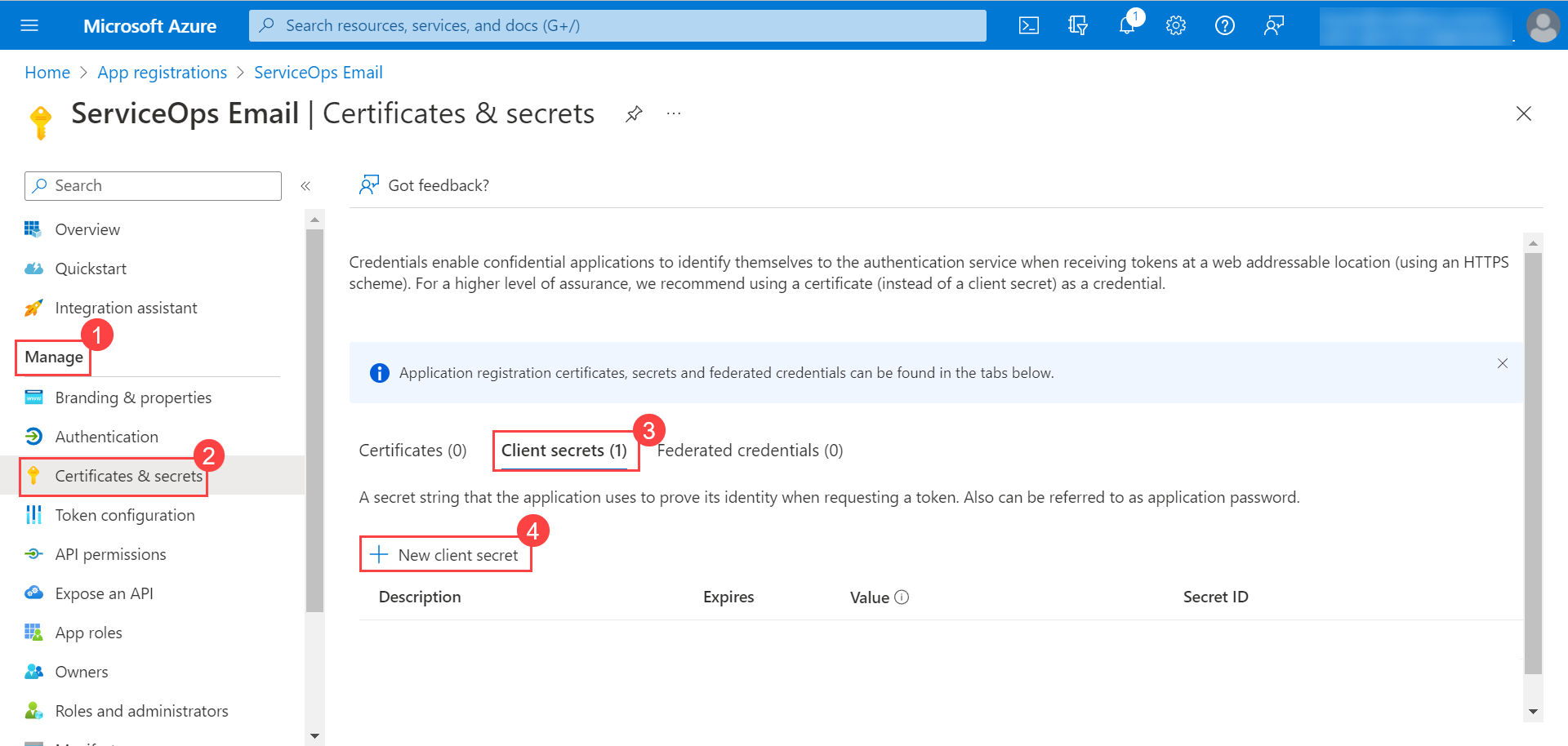
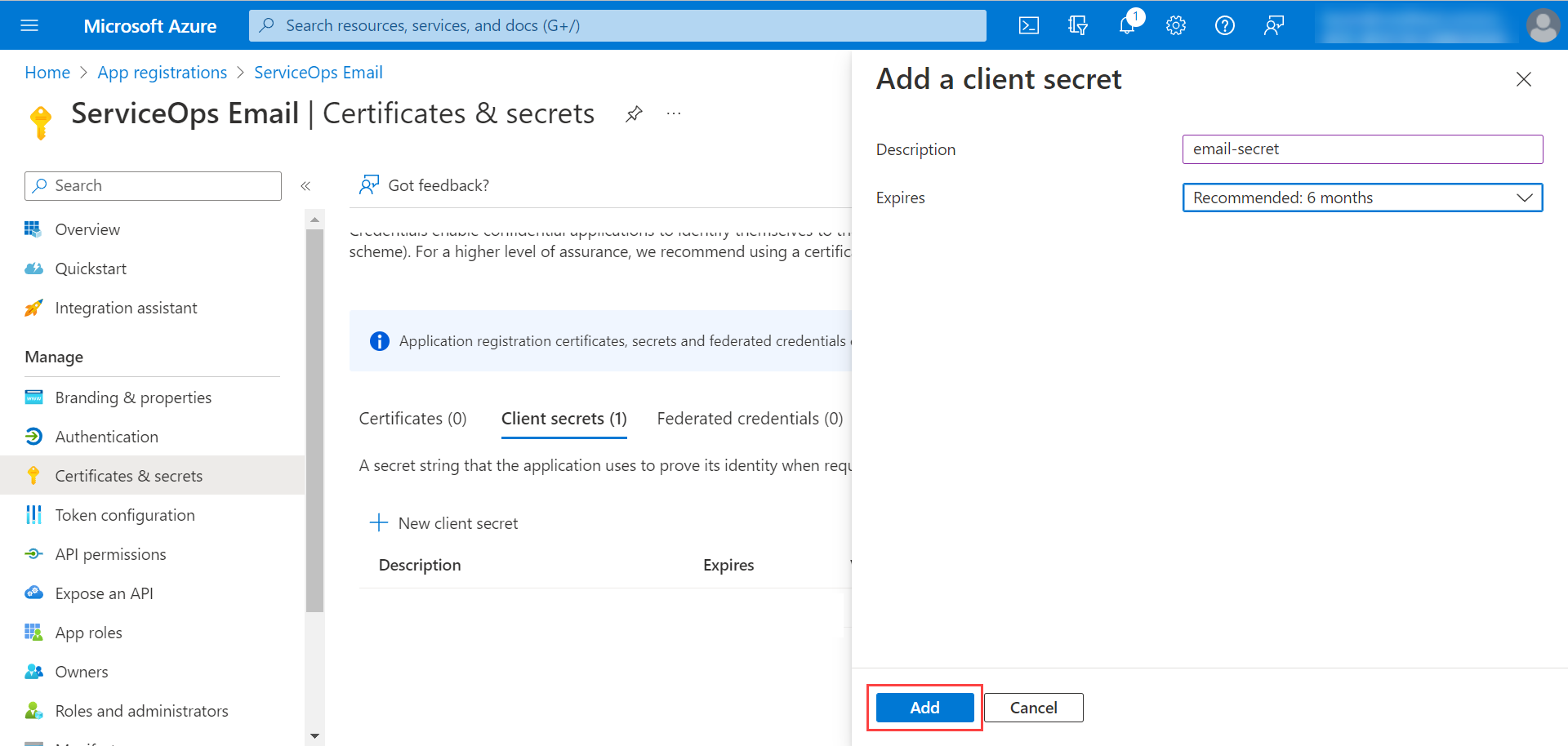
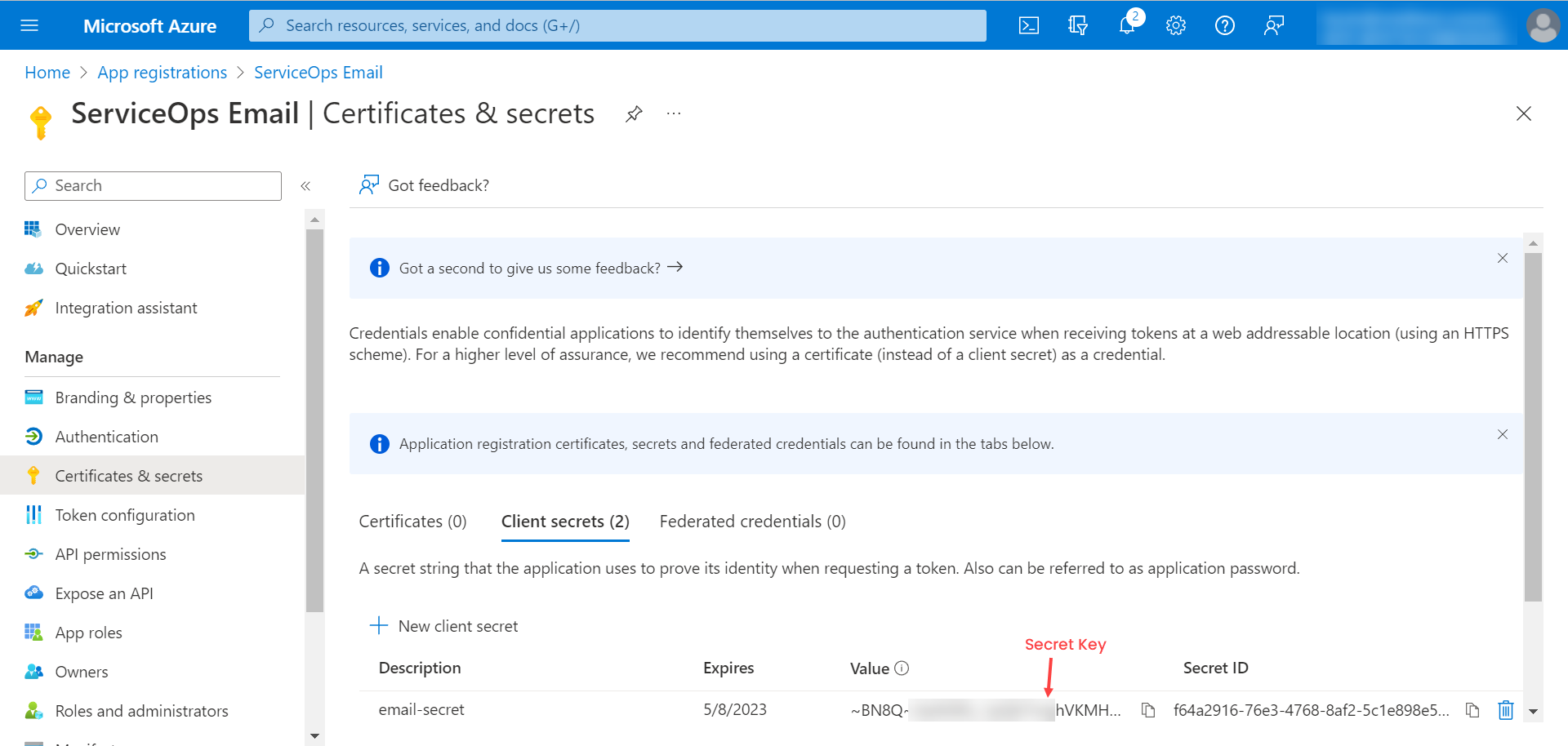
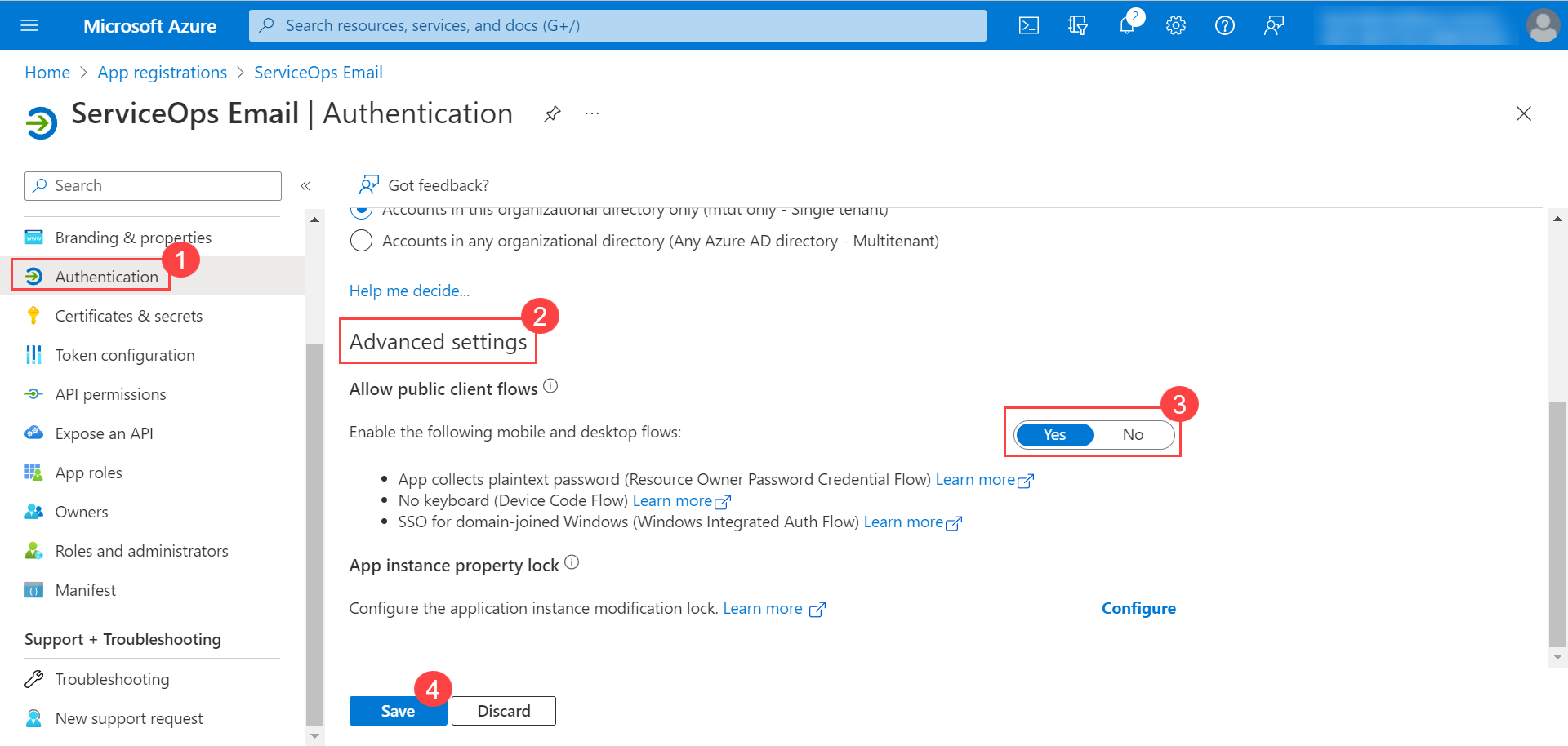
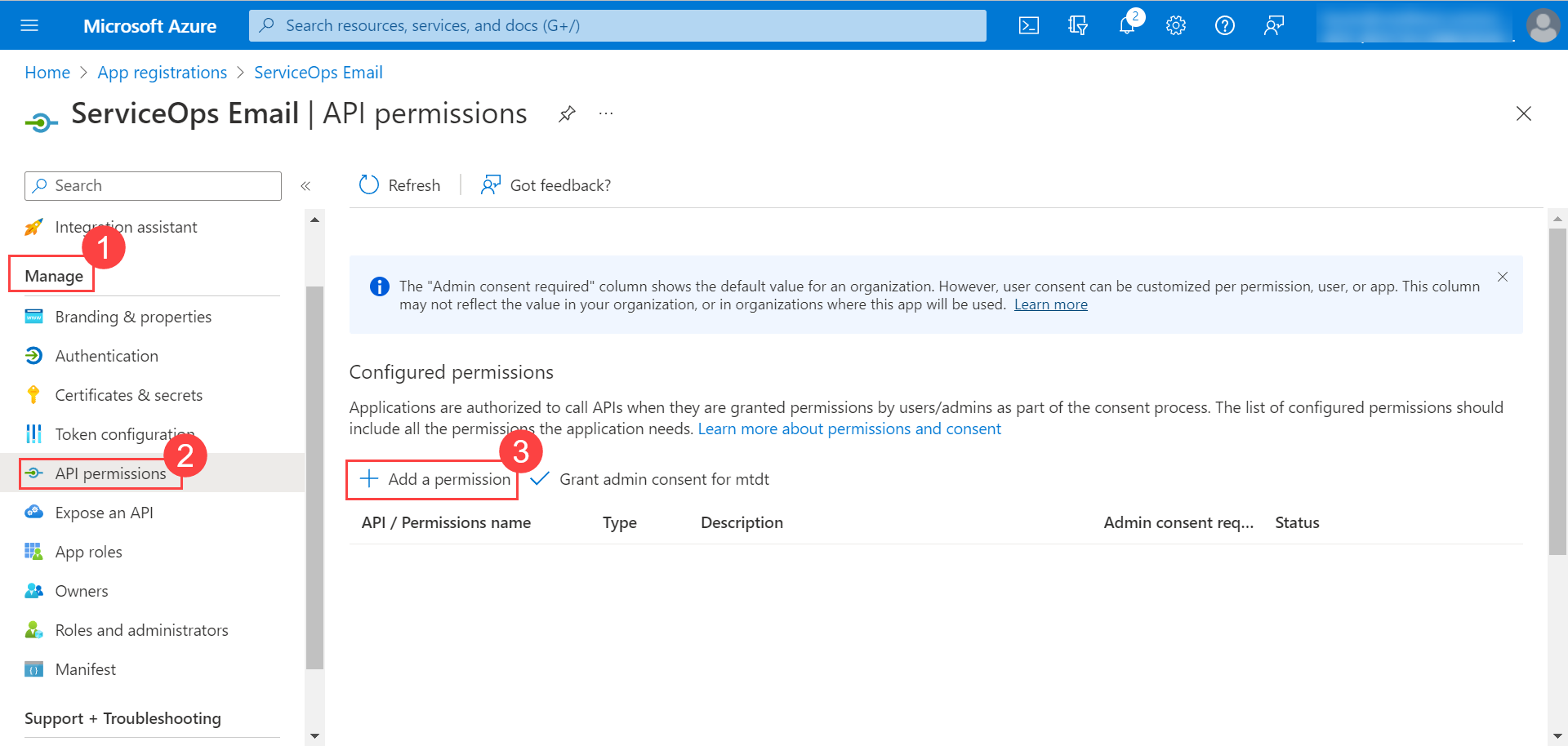
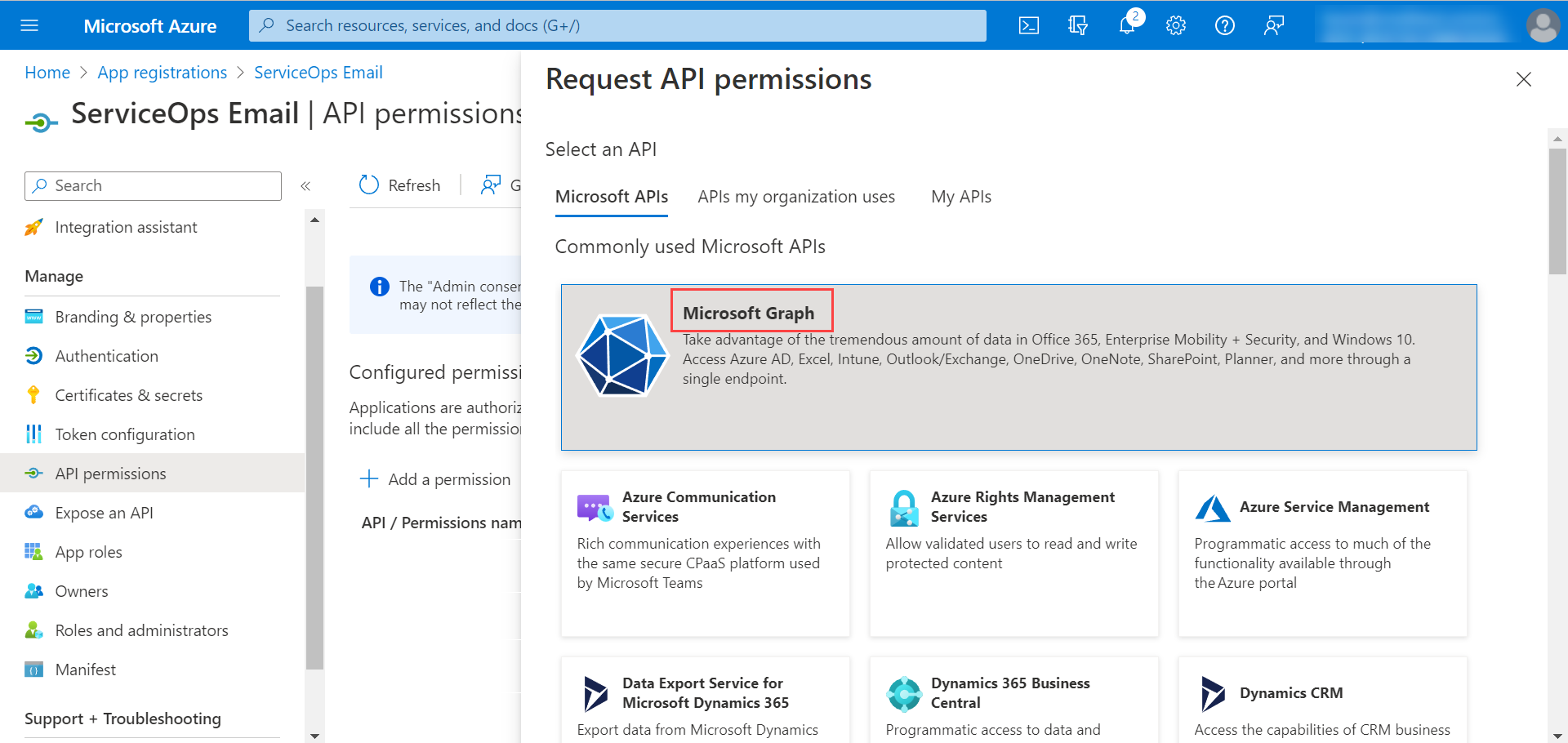
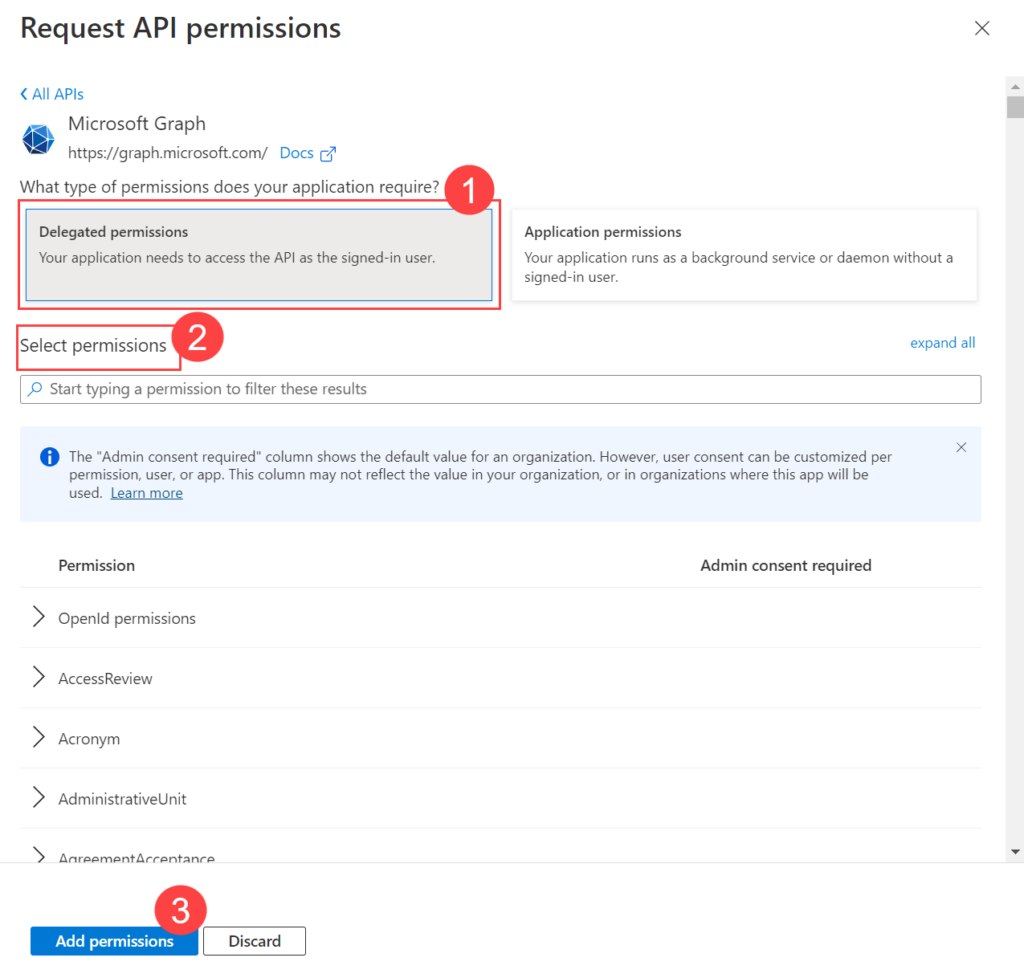
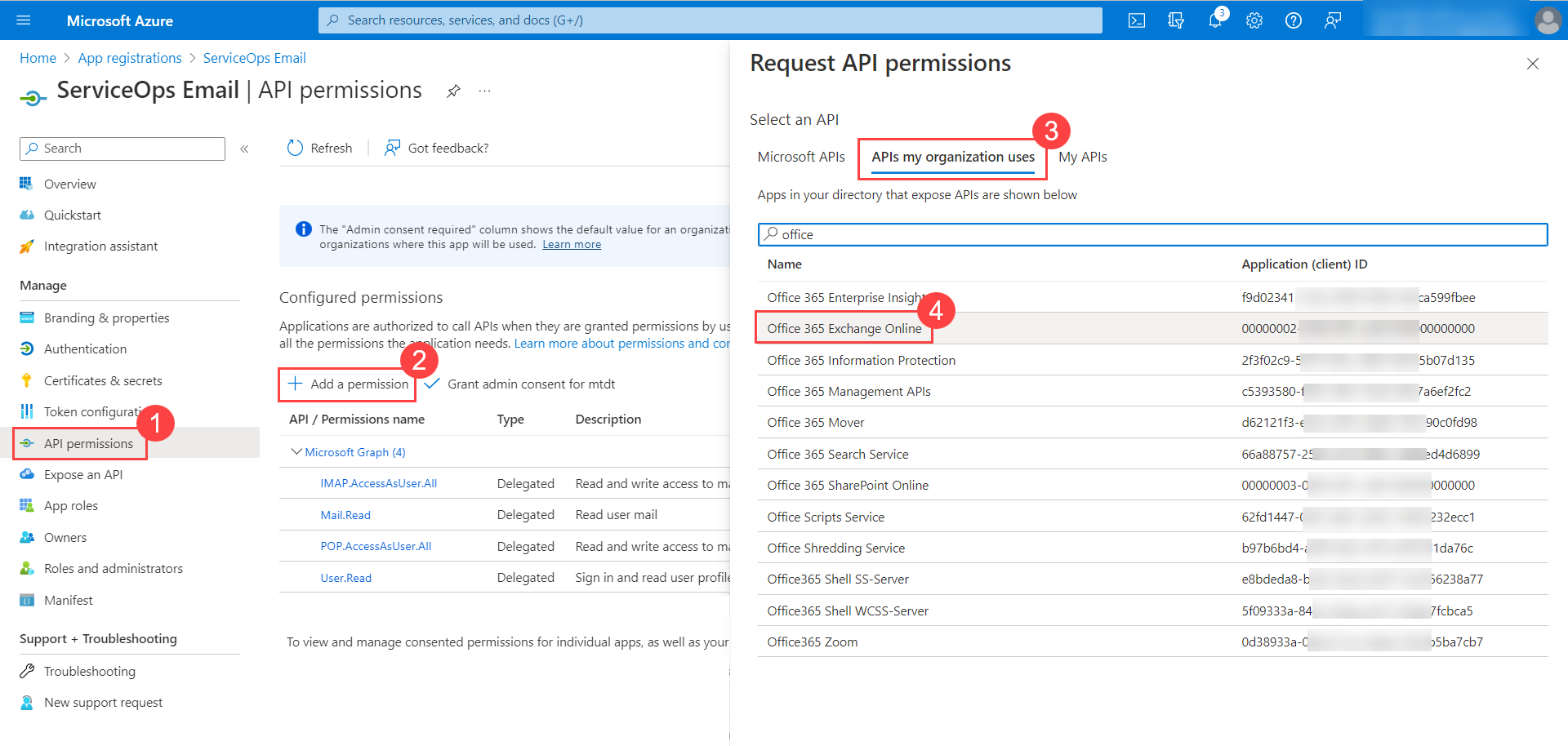
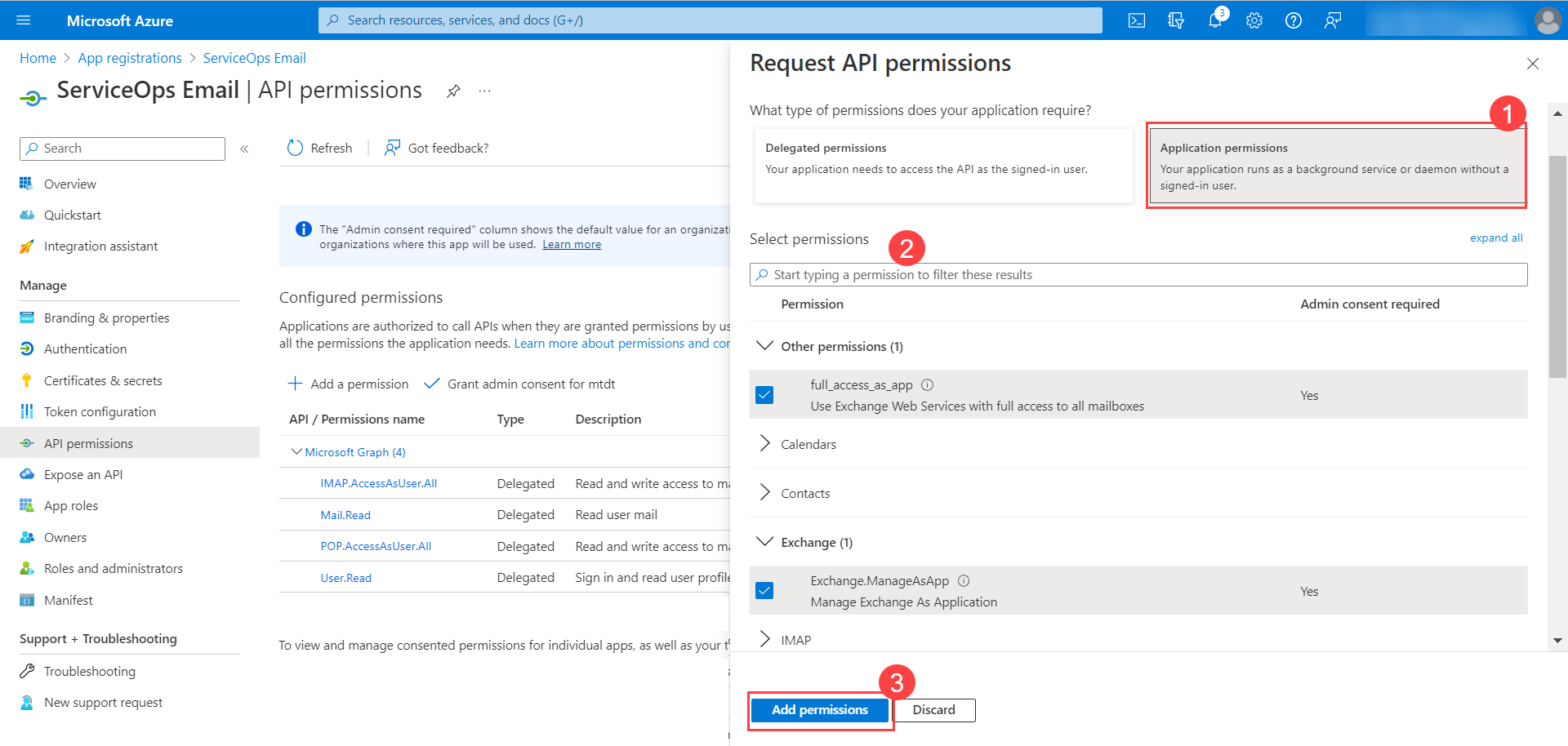
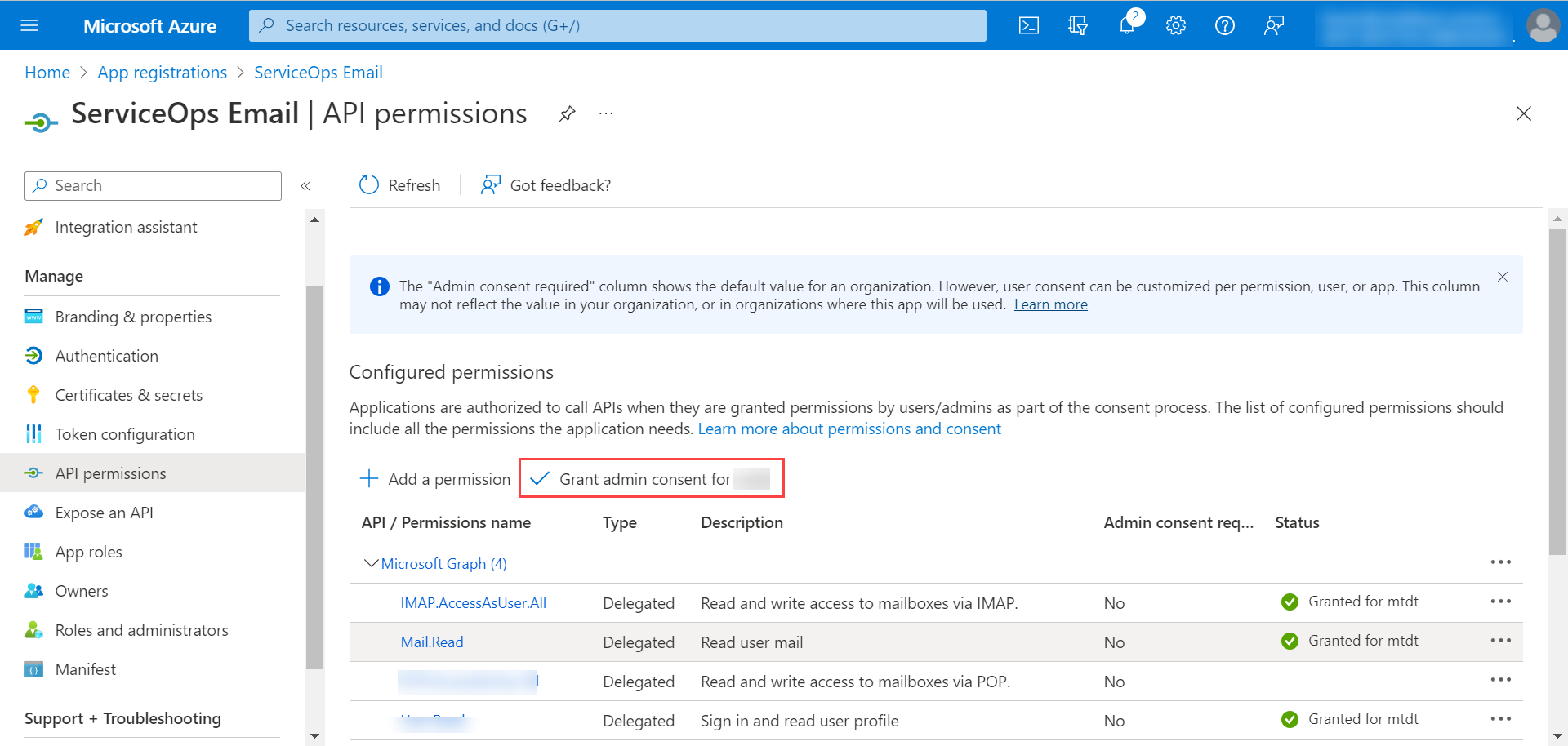
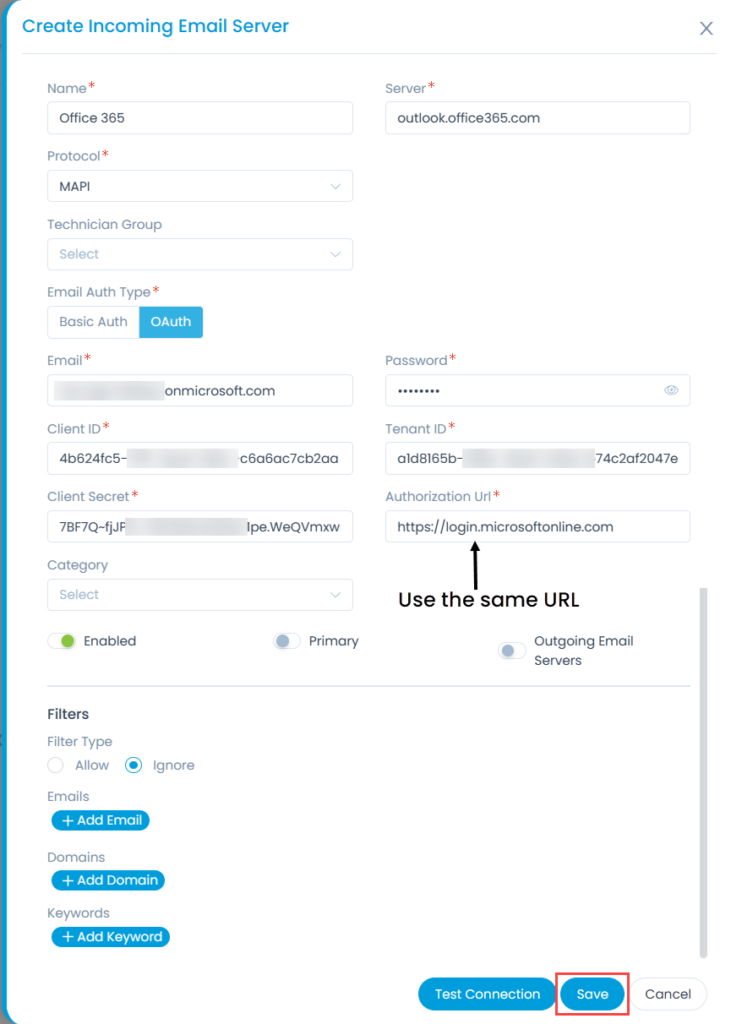
Configuring Microsoft Azure for OAuth
What is Microsoft Azure?
Microsoft Azure is a public cloud computing service owned by Microsoft. It provides a wide range of cloud services, including analytics, storage, computing, and networking.
What is OAuth?
OAuth is an Open Standard Authorization protocol that allows you to authenticate one application communicating with another on your behalf without sharing the password. It uses client secret values instead of a password to allow access to a secured resource. Thus, the email communication will be secured.
This functionality is applicable from version 7.9 and above.