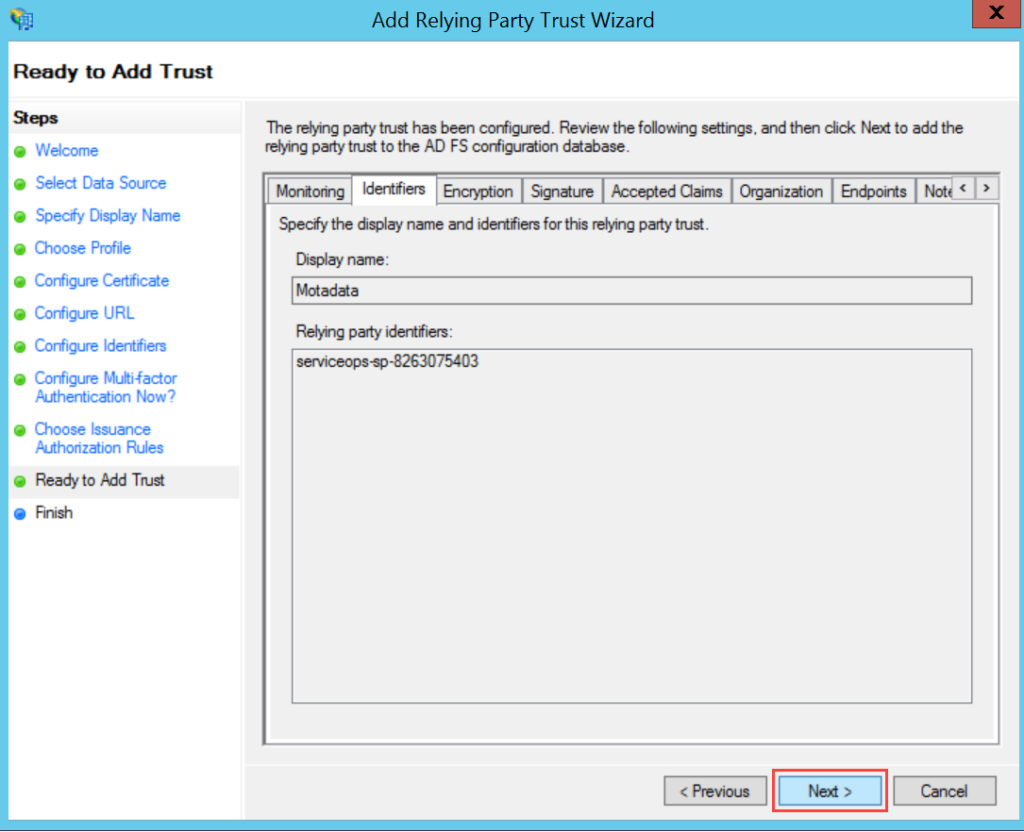
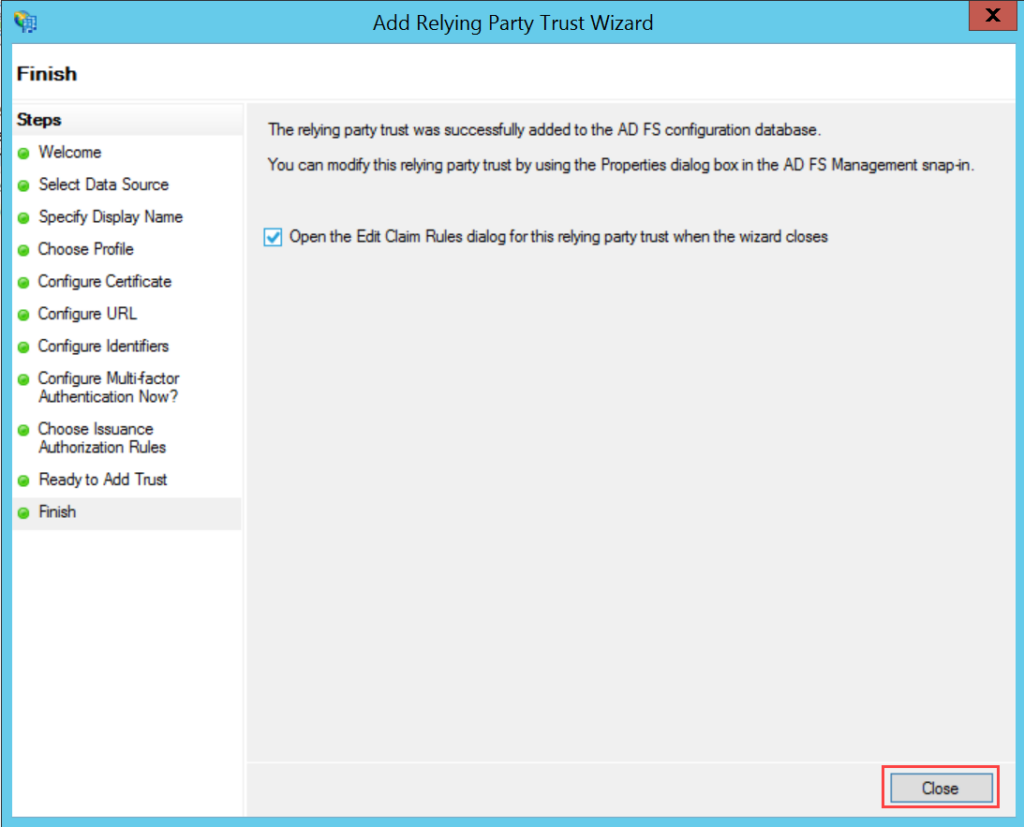
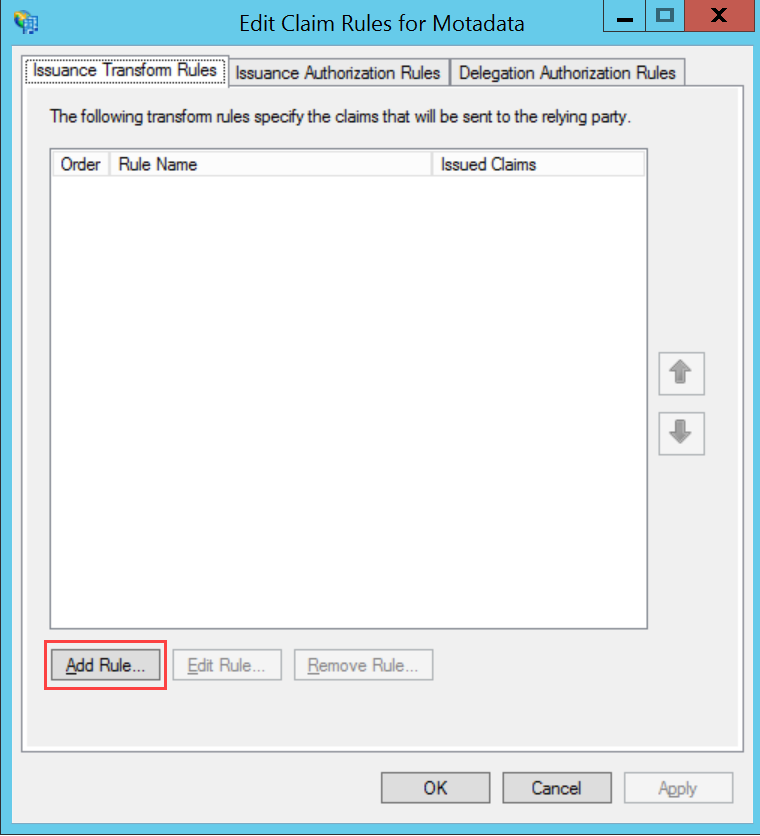
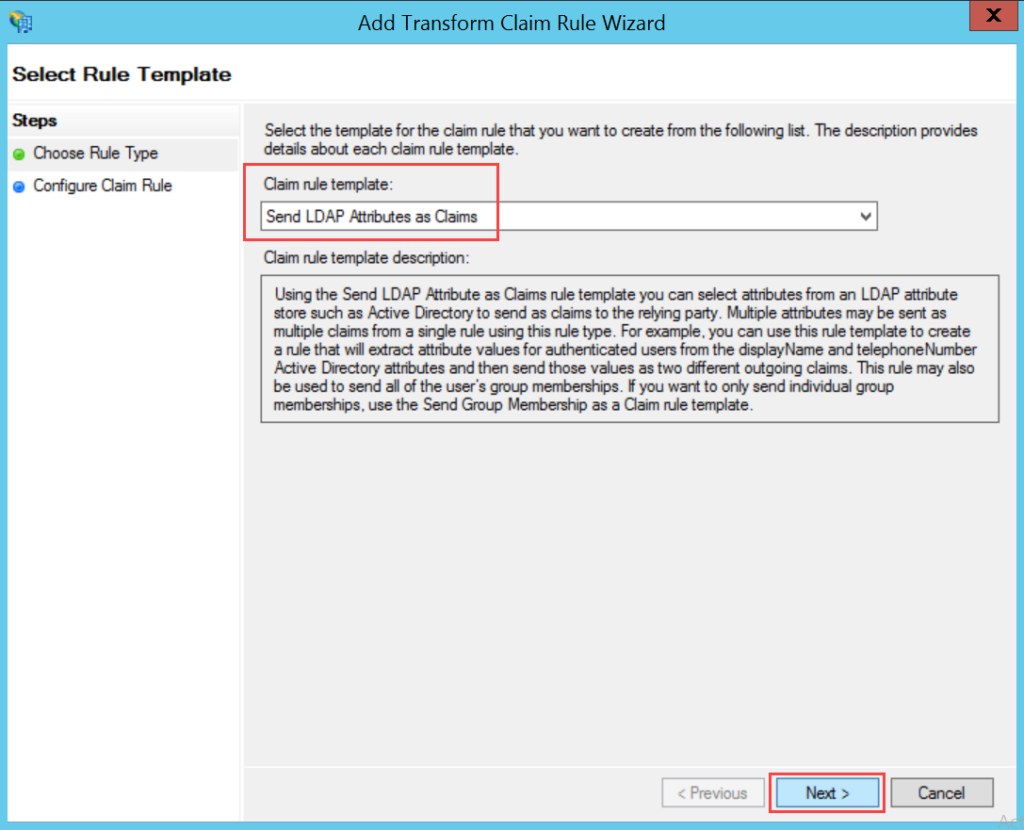
ADFS
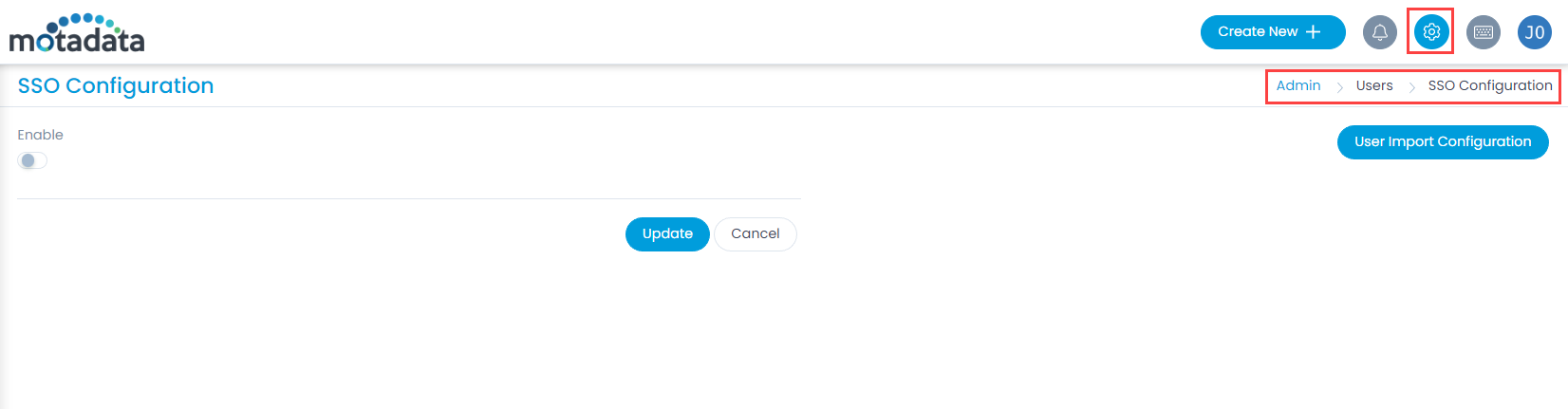
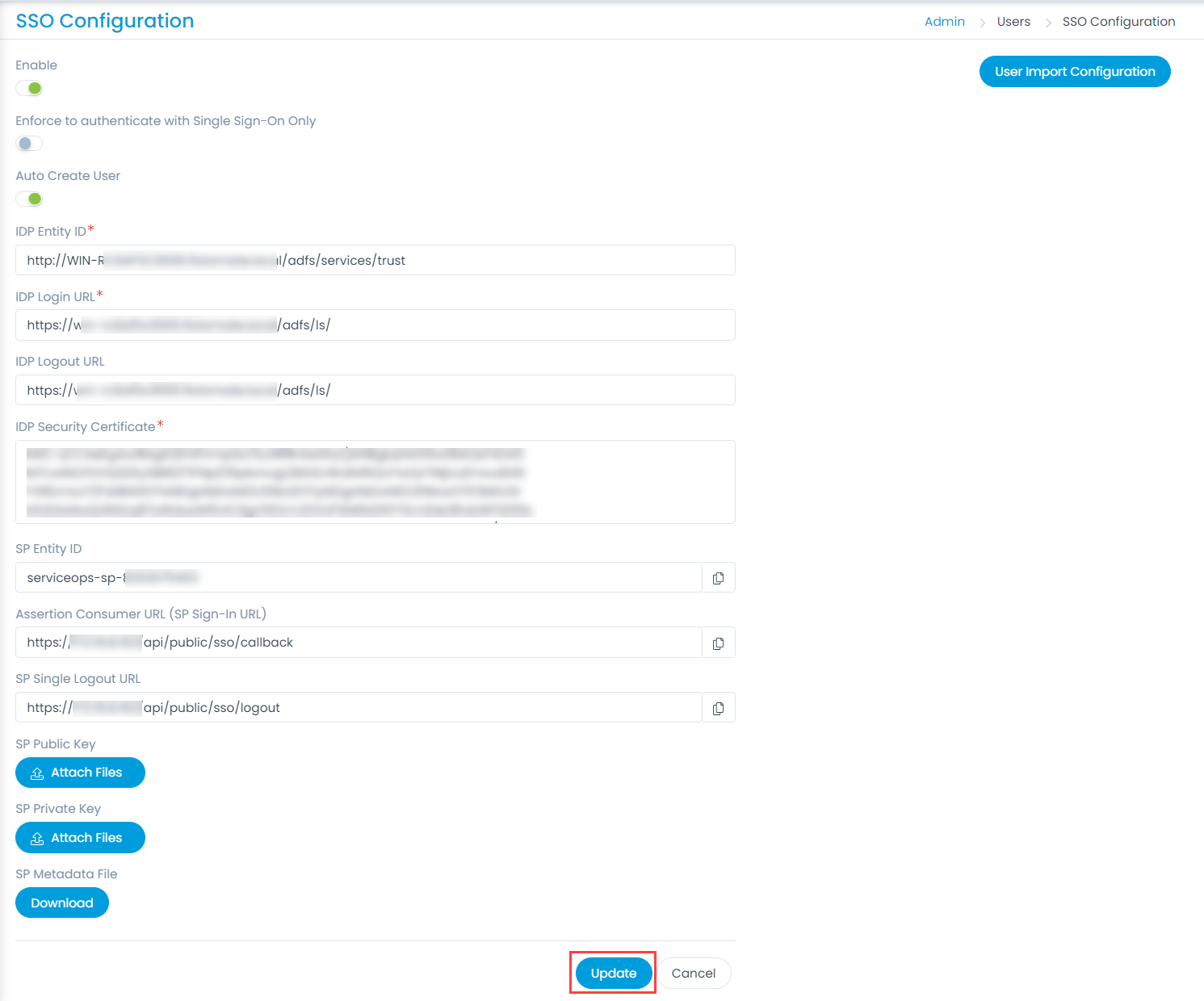
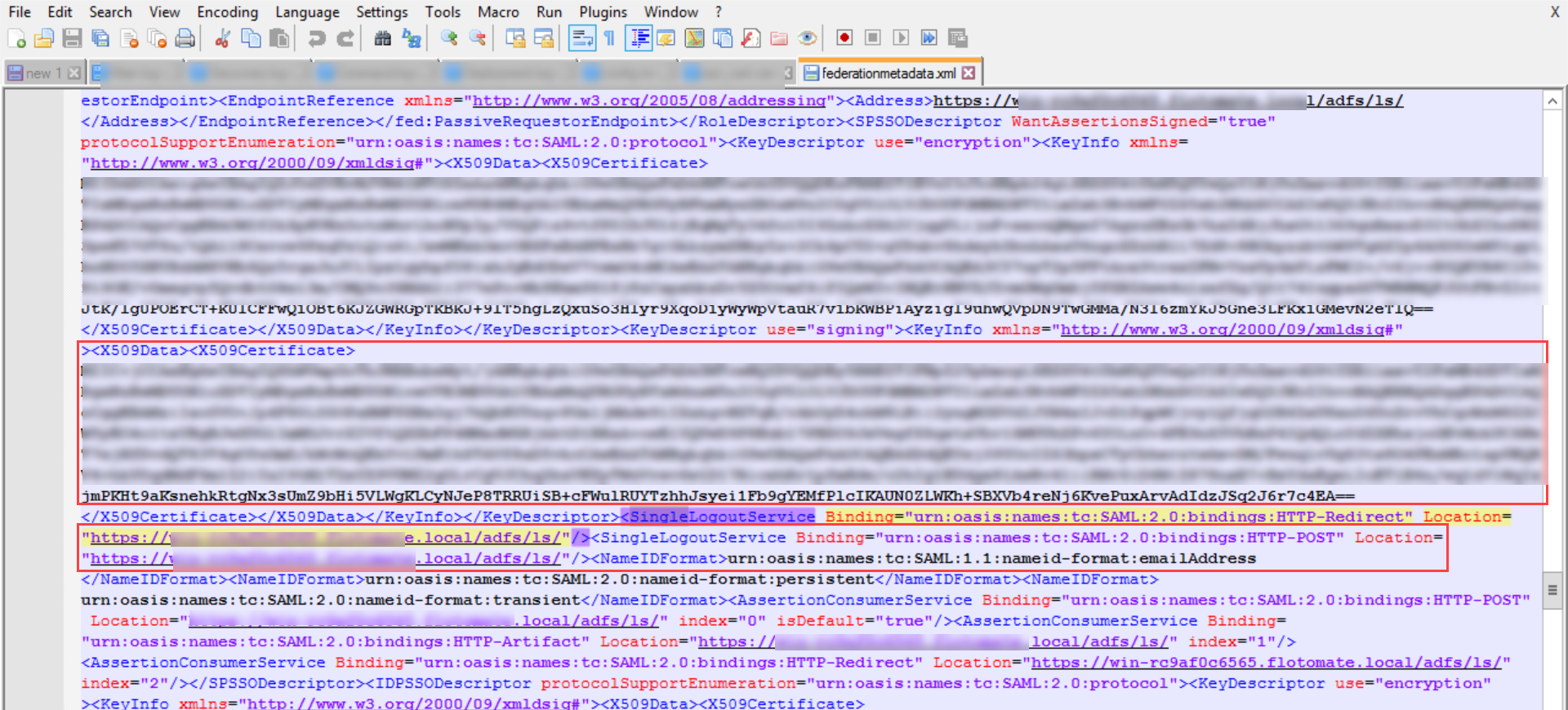
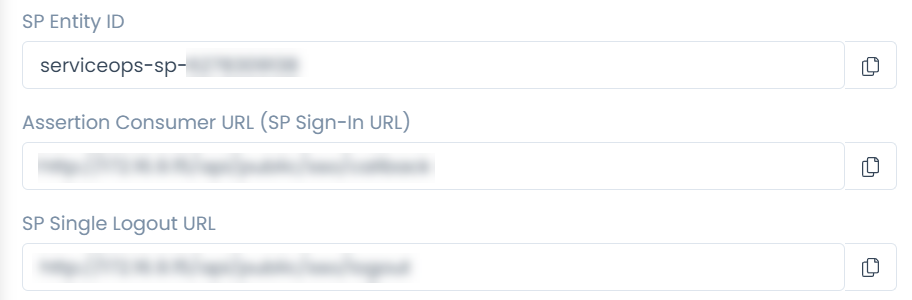
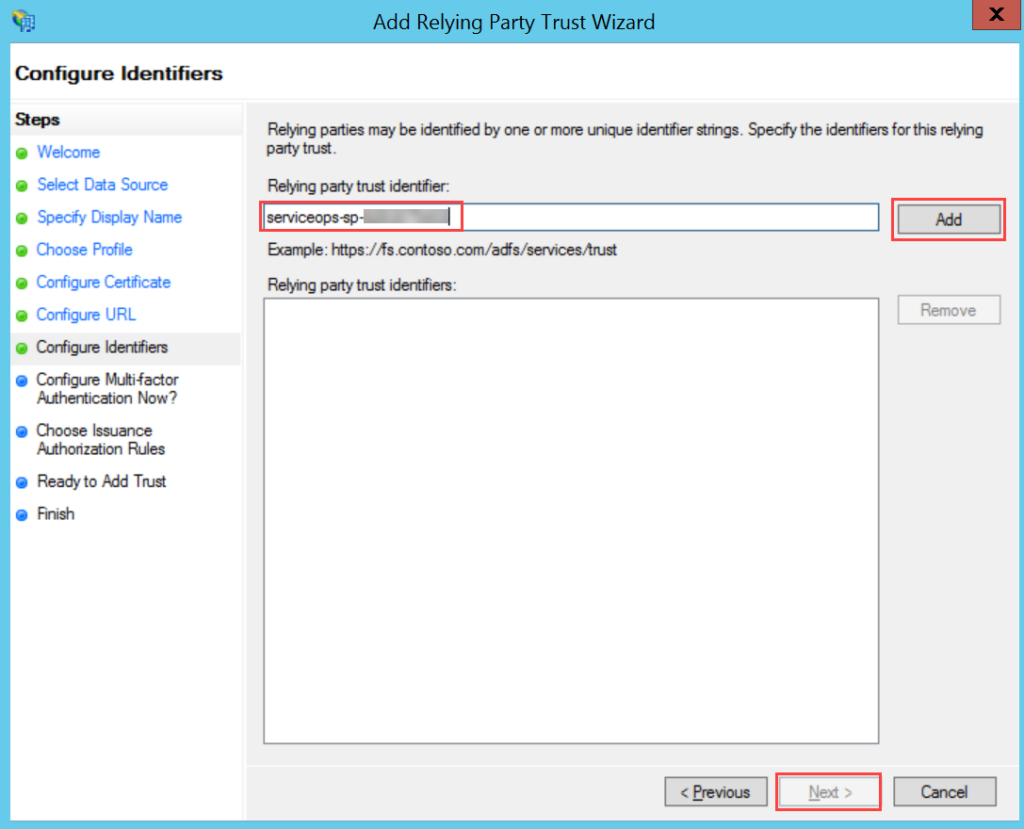
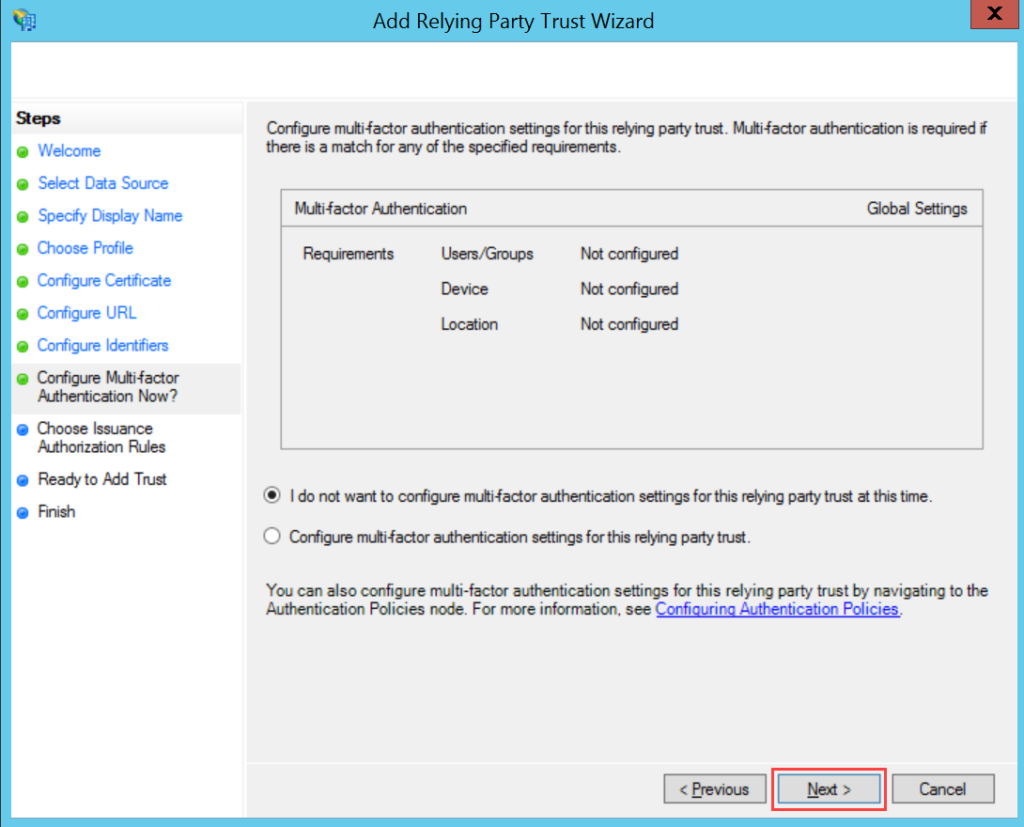
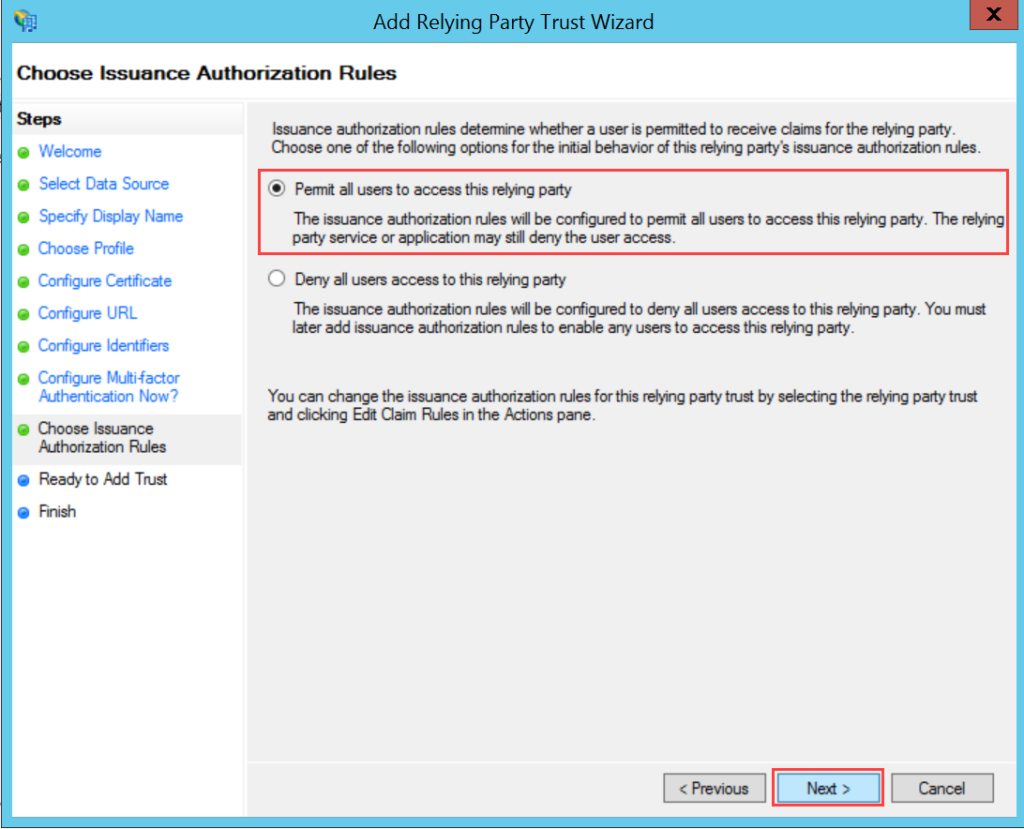
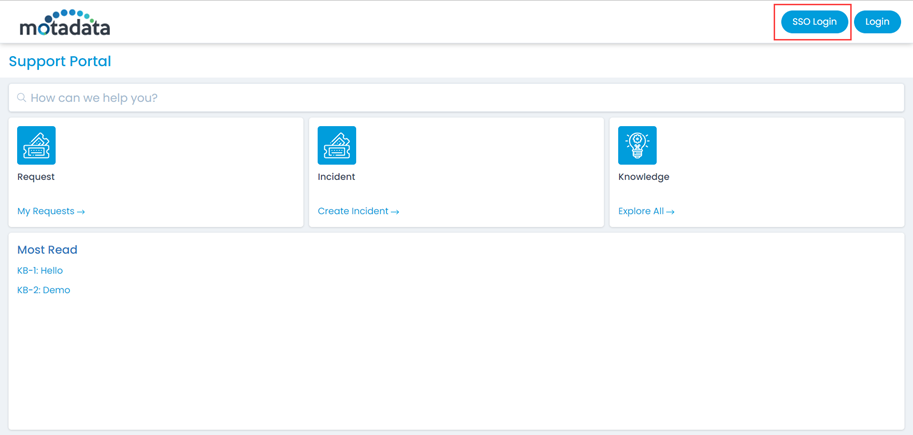
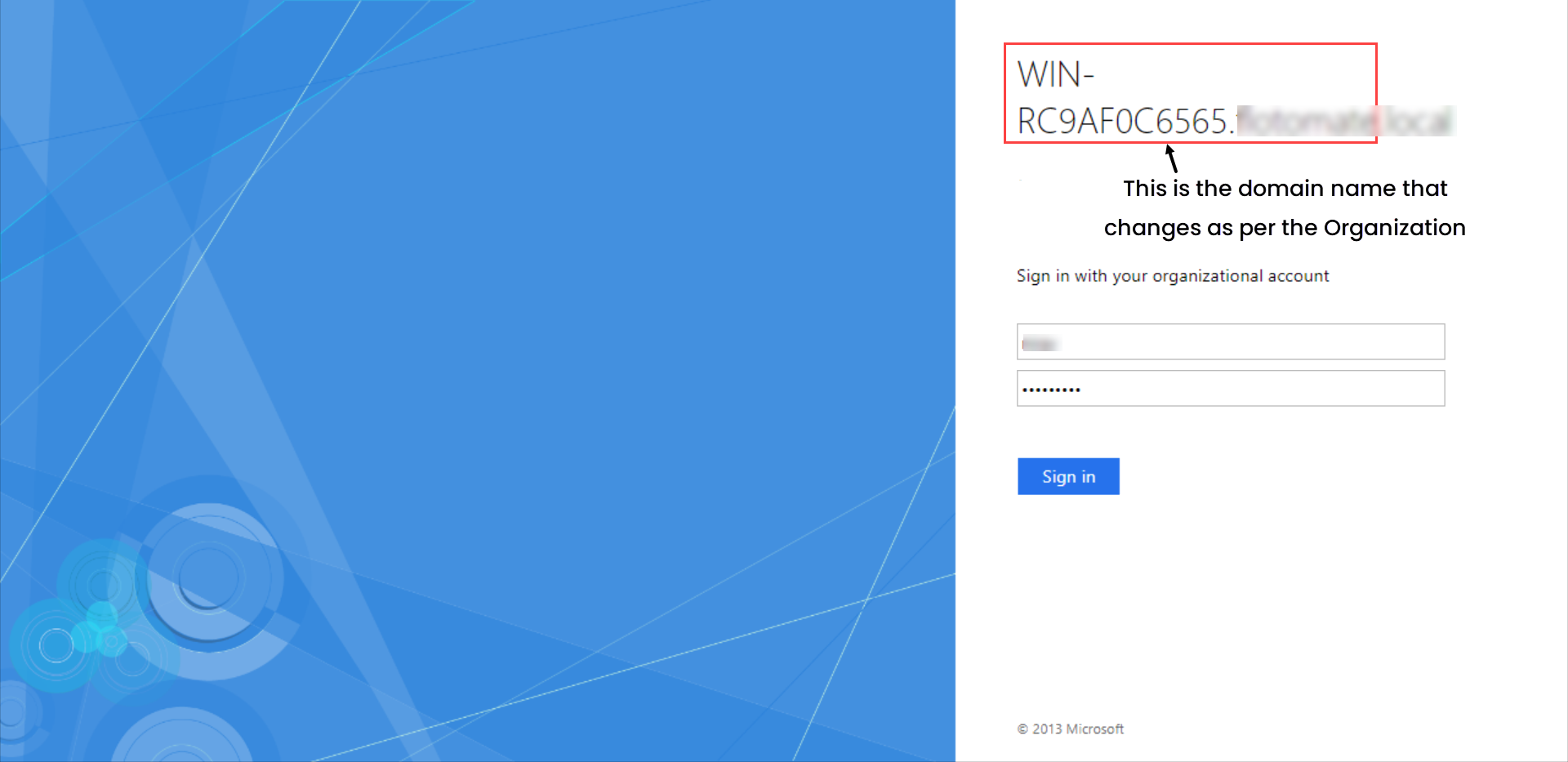
ServiceOps offers support for SAML 2.0, which facilitates integration for Single Sign-On. ServiceOps acts as the Service Provider (SP) and it integrates with Identity Providers (IdP) using SAML 2.0. The integration basically involves supplying details about SP to IdP and vice-versa. Once you integrate ServiceOps with an IdP, the users simply have to sign-in to IdP and then, they can automatically sign-in to ServiceOps from the respective identity provider’s GUI without having to provide credentials again. ServiceOps supports integration with ADFS.
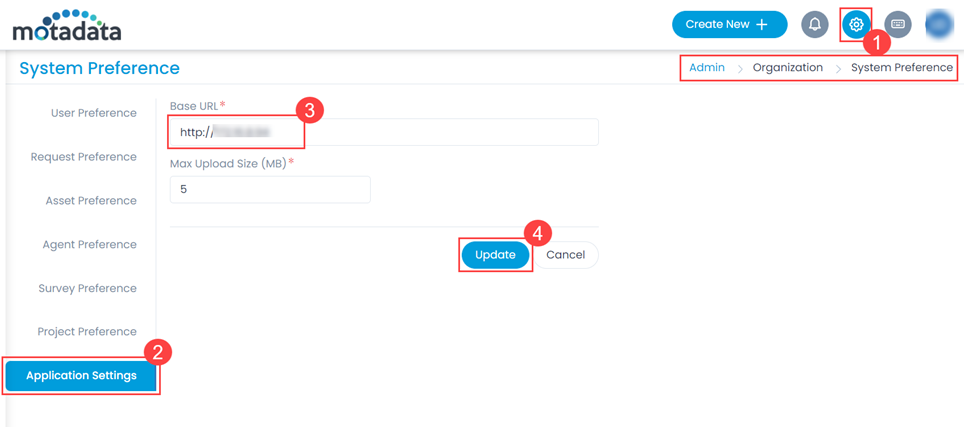
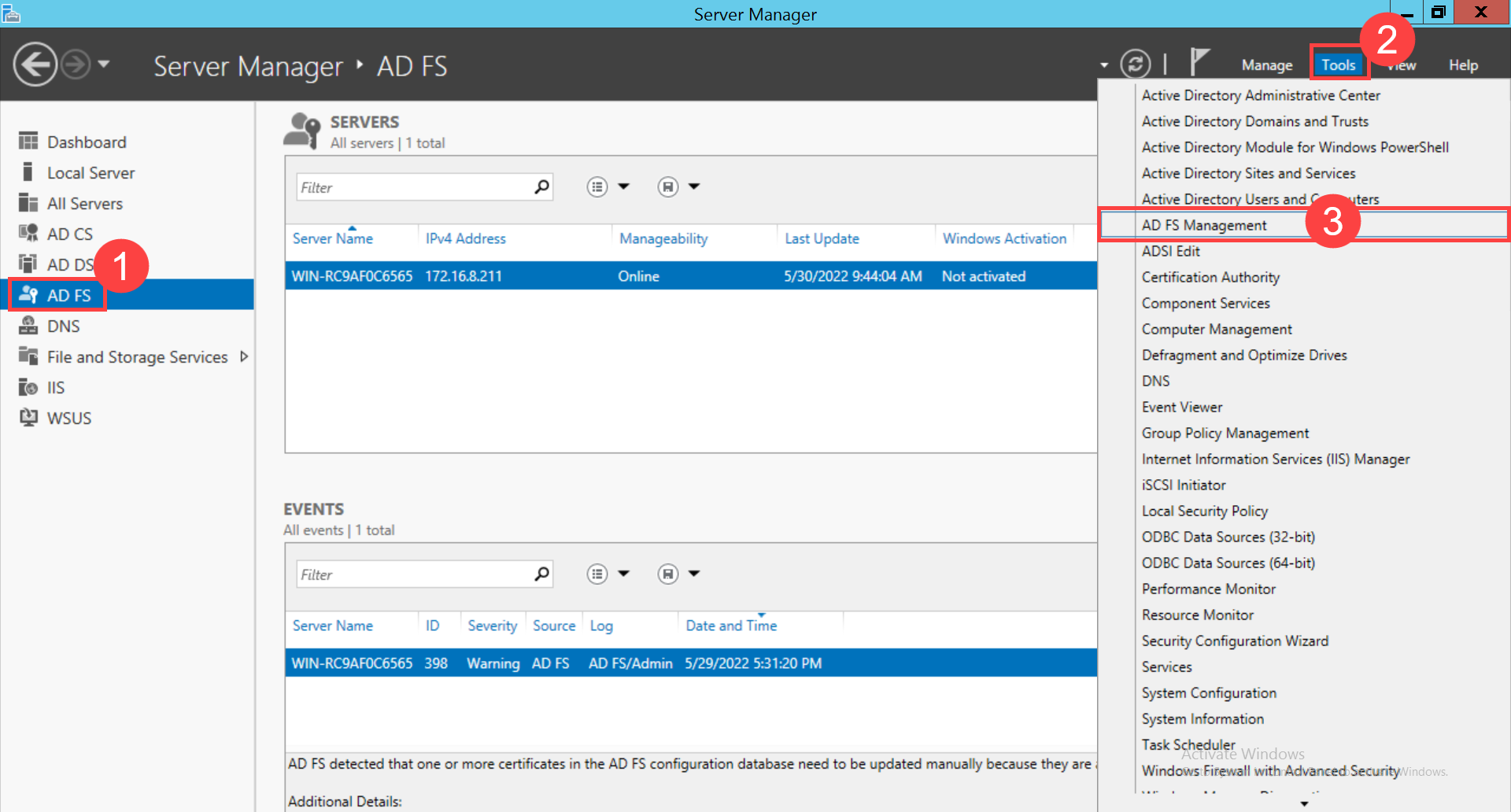
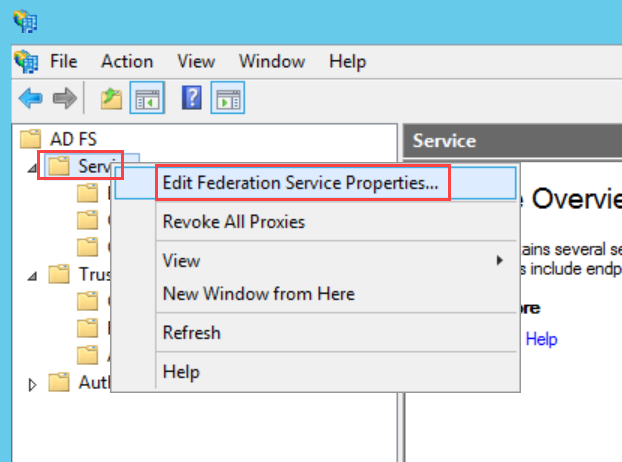
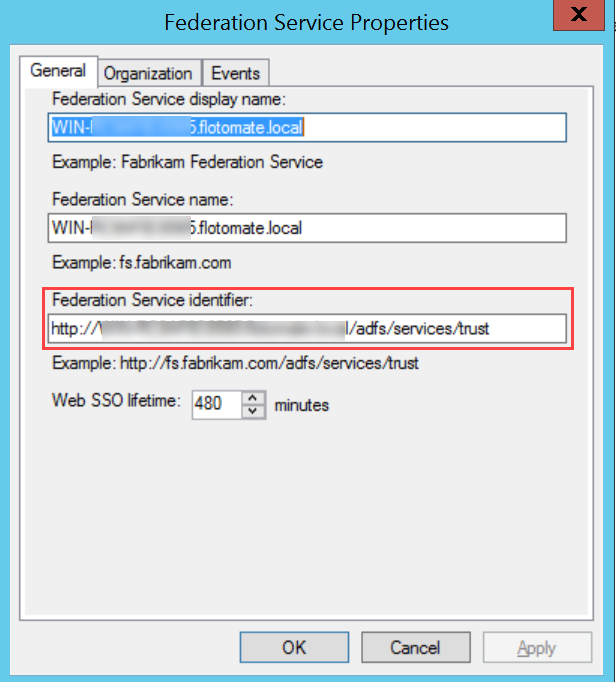
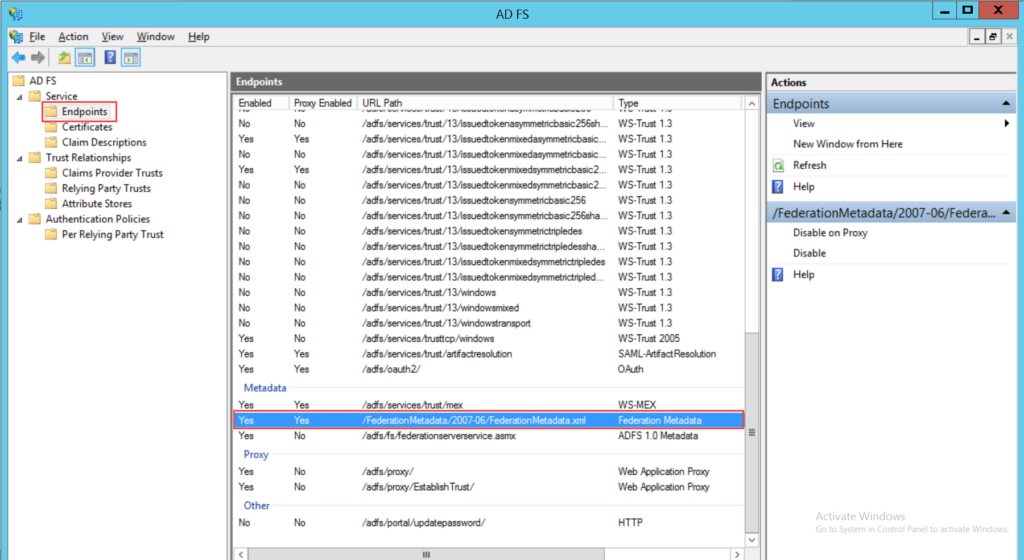
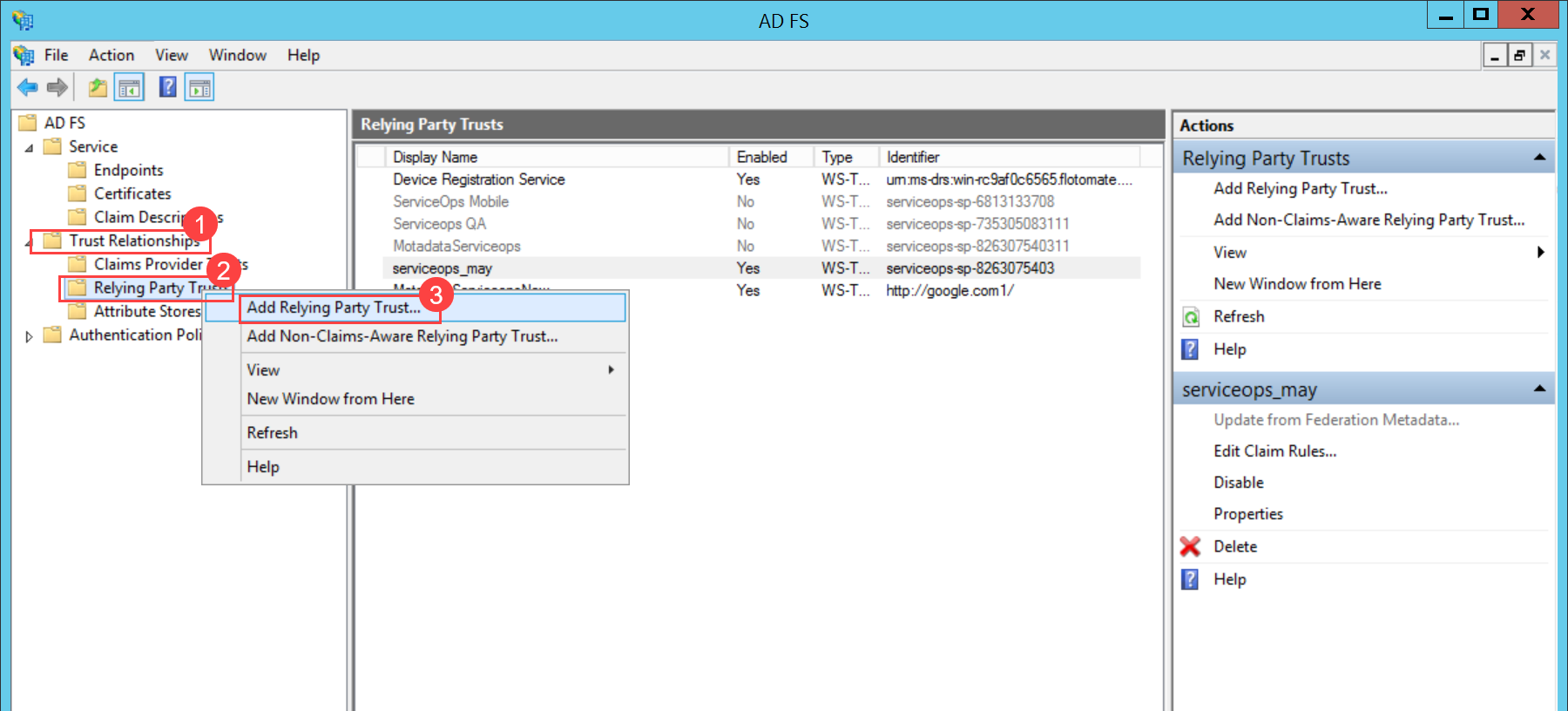
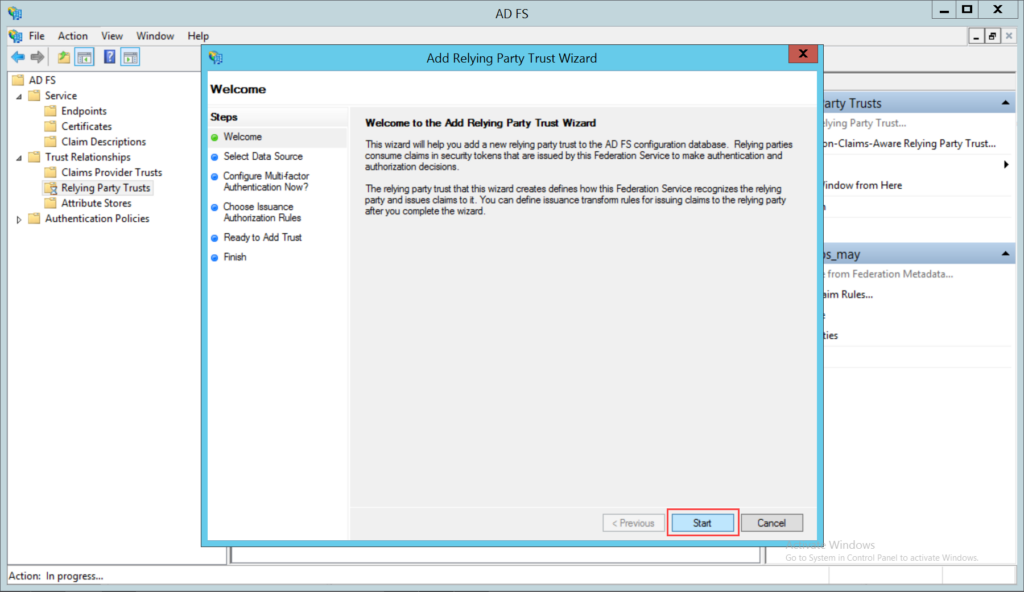
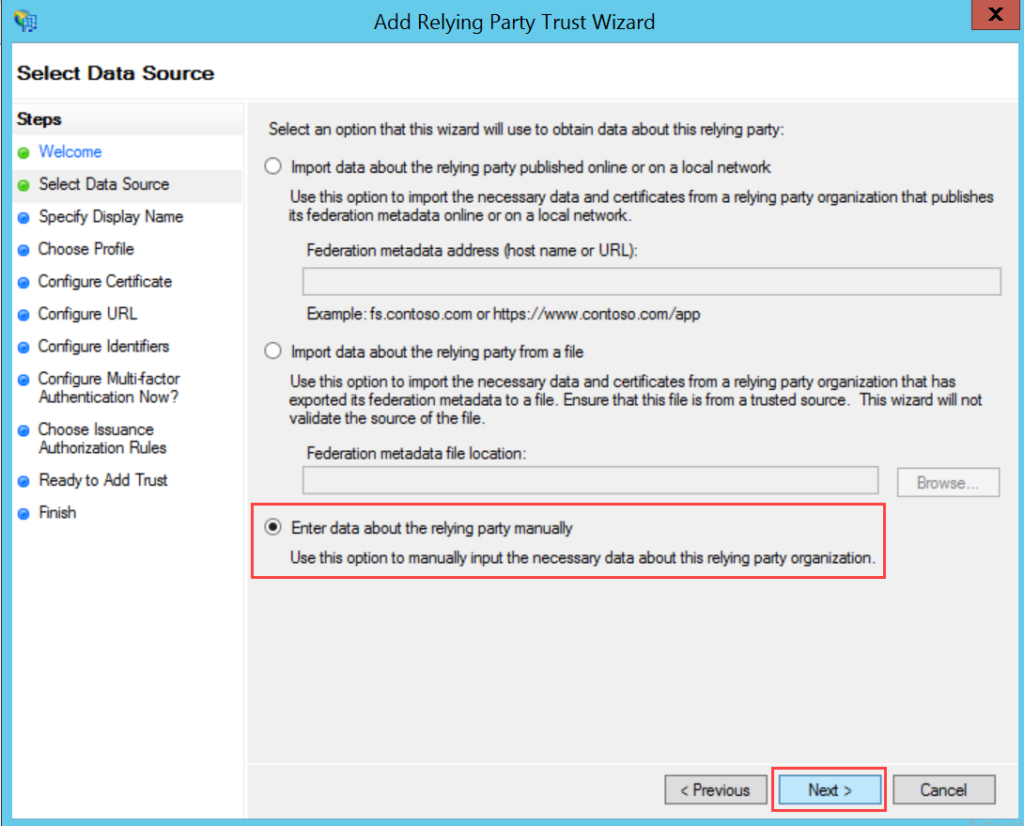
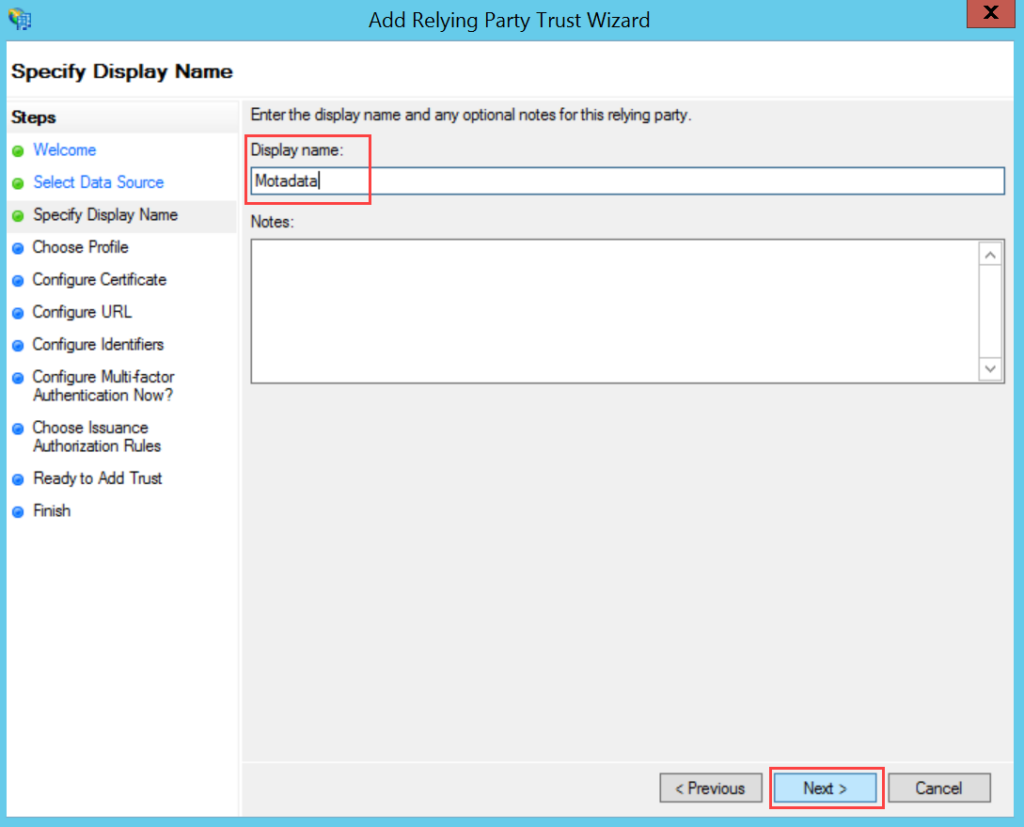
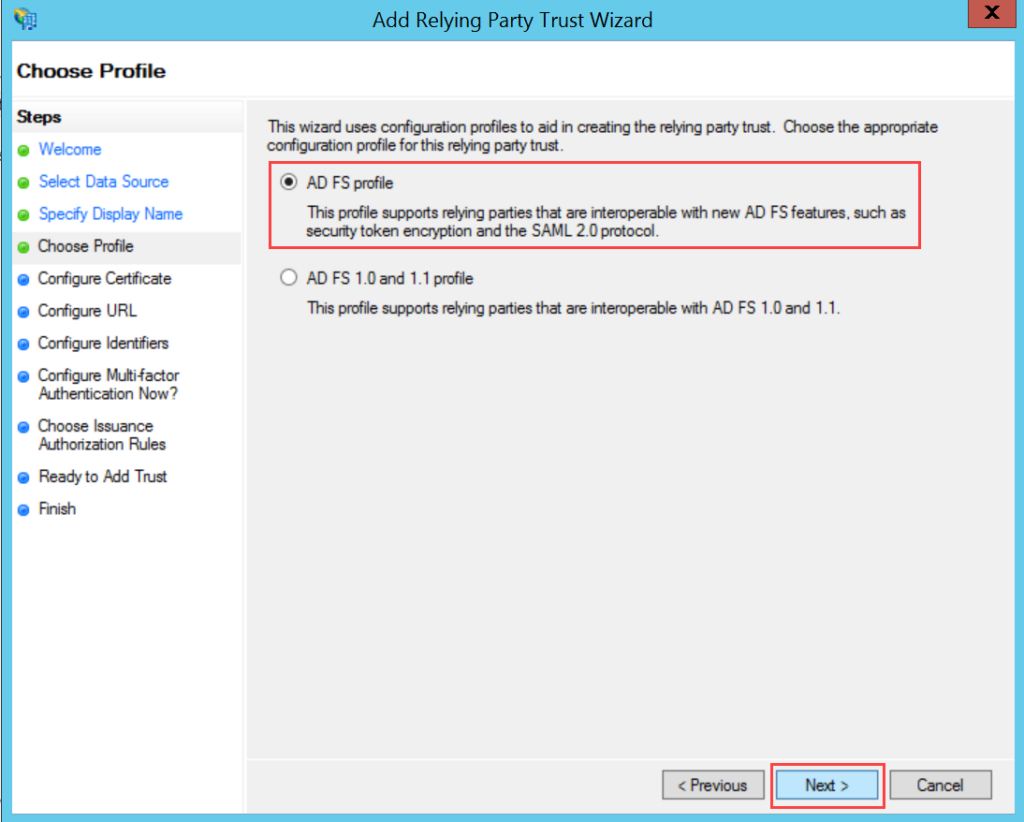
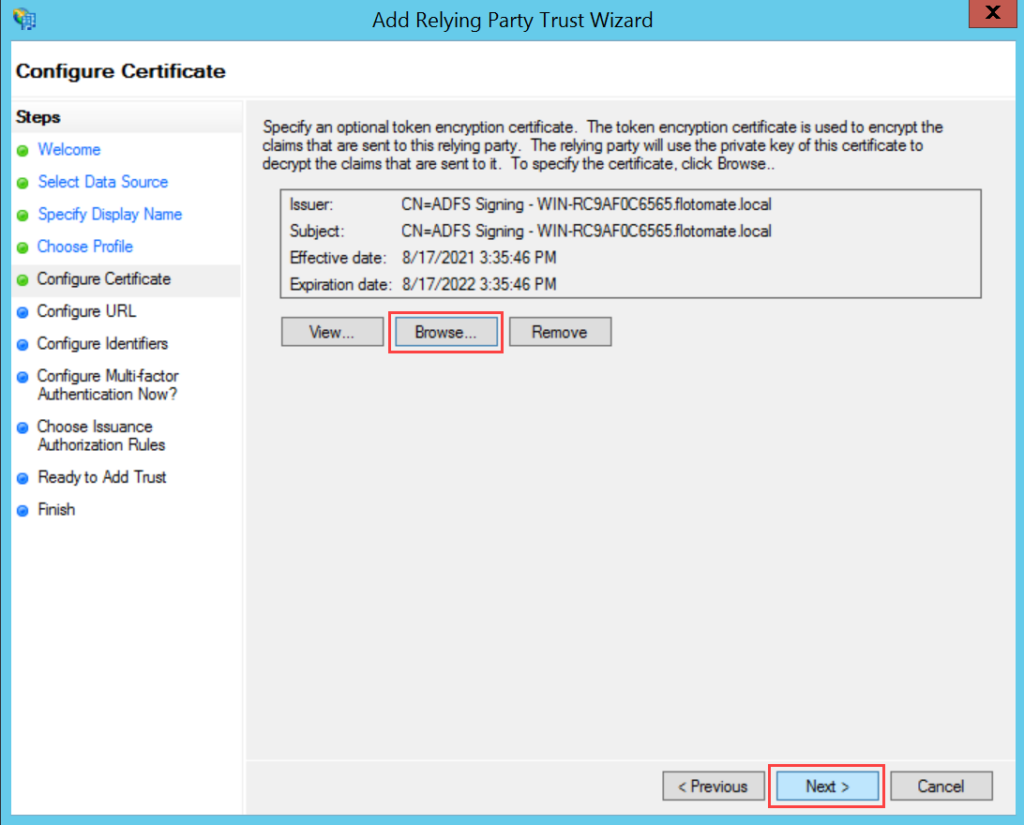
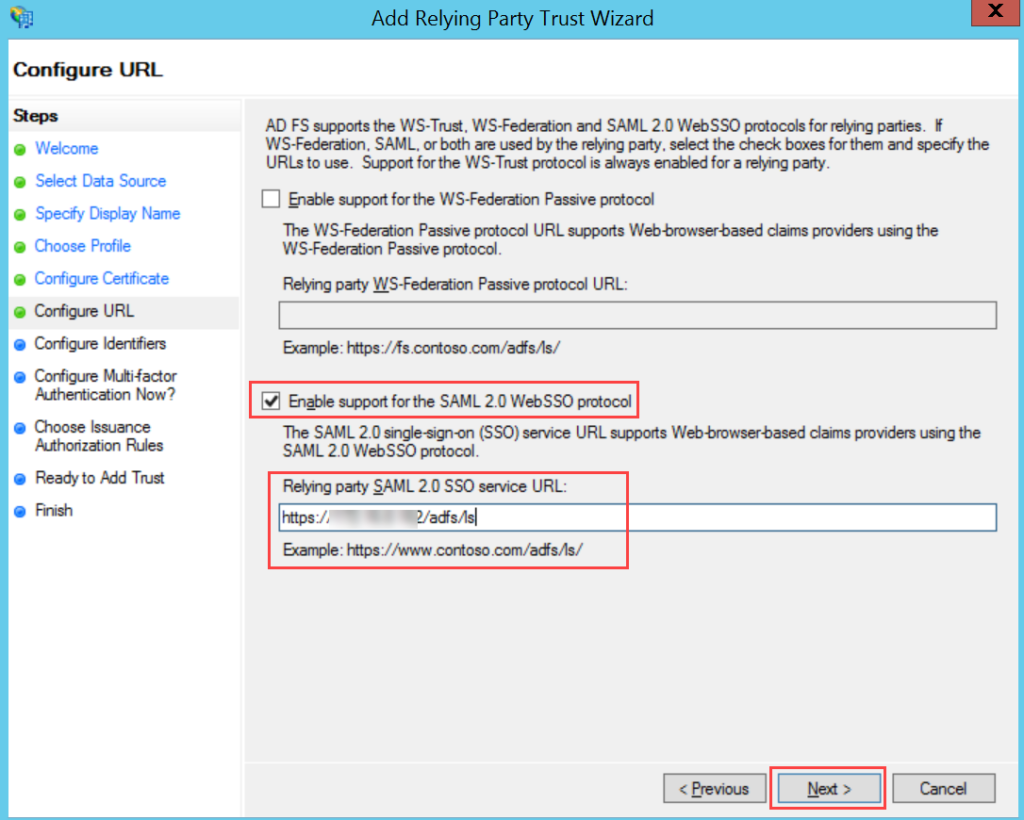
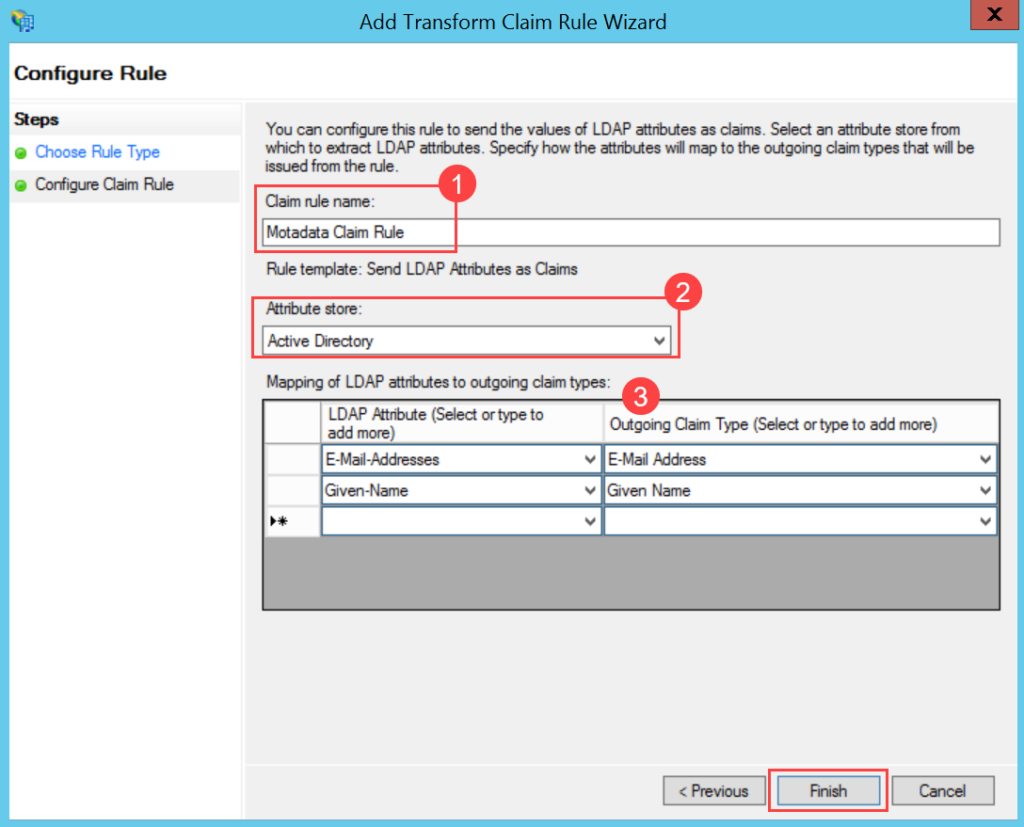
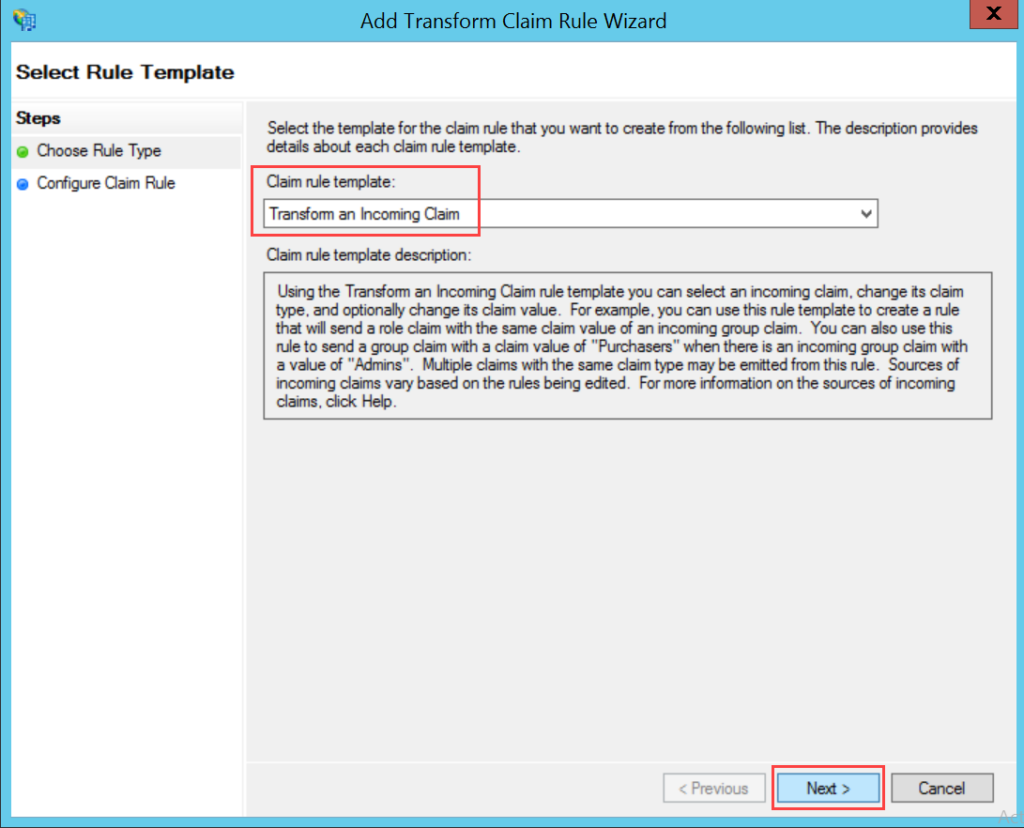
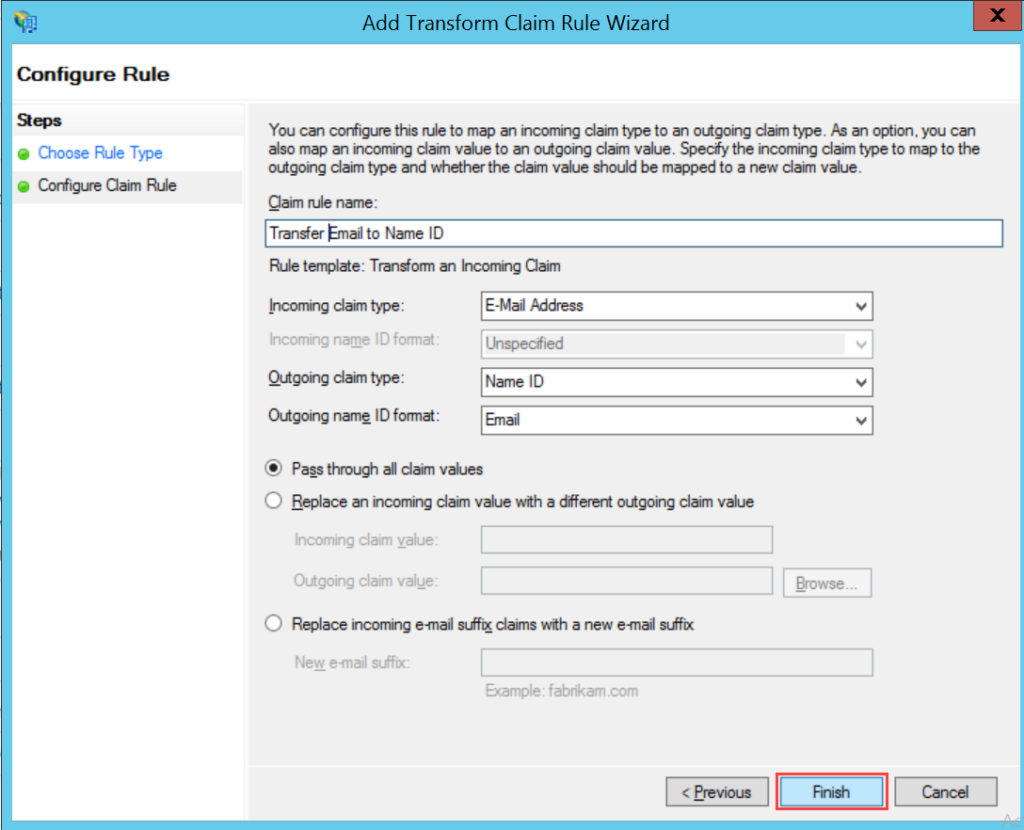
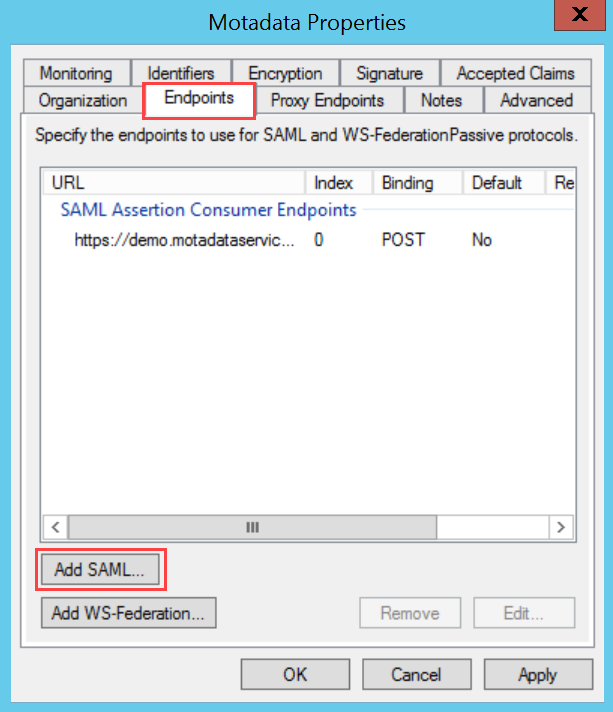
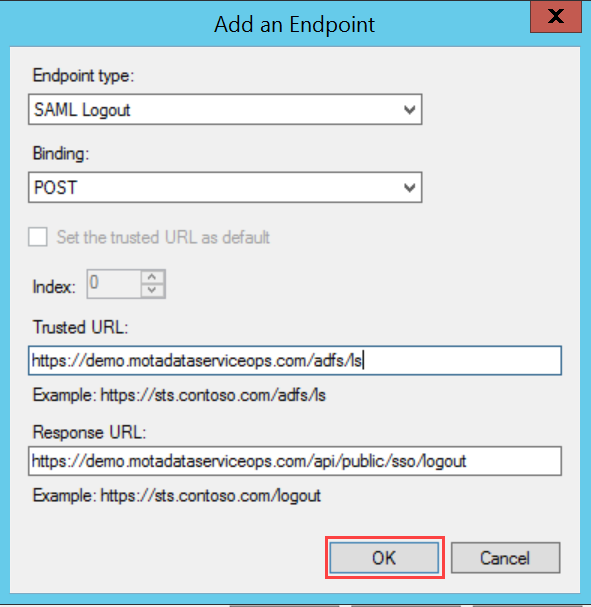
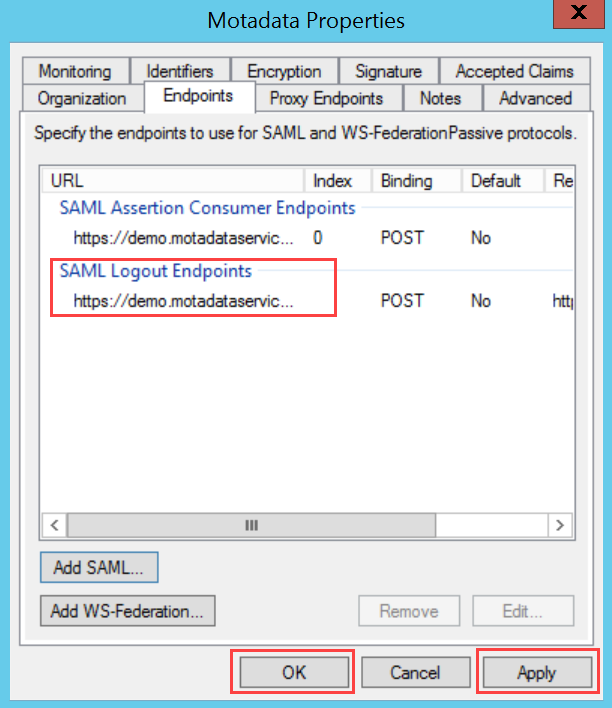
To configure SSO with the ADFS service, follow the below steps:
- Sign-in to the ServiceOps portal as a Technician.