What is Syslog Monitoring?
Syslog, also known as System Logging Protocol, is a standard protocol widely used for logging and transmitting messages from network devices, servers, and applications to a centralized server or device, known as a Syslog server. It is commonly used in Unix-based systems and network devices and is also supported in many other operating systems and applications.
Various system components and applications generate Syslog messages, typically containing information about events, errors, warnings, and other important system activities.
These messages can be transmitted over different transport protocols, such as UDP or TCP, and they are usually stored in plain text files or a database.
As the Syslog protocol contains essential network data and is responsible for networking transmission, it becomes vital to monitor Syslog data. Syslog network monitoring is collecting, analyzing, and managing Syslog messages generated by various network elements.
Motadata helps you configure the Syslog servers and agents installed to capture and forward Syslog messages to a central repository to analyze them and get powerful, actionable insights.
Why is Syslog Monitoring Important?
Syslog monitoring is an essential aspect of network and system management, as it allows administrators to identify and troubleshoot issues quickly and to ensure that systems are operating within expected parameters. It can also be used to track system performance and activity over time, which can help identify trends and optimize system performance.
Motadata AIOps is a complete Syslog Management tool that helps you configure Syslog protocol and let system administrators specify which messages are logged, where they are sent, and how they are stored. It also involves message filtering and categorization based on severity levels, facilities, and other parameters.
Overall, Syslog monitoring provides a centralized platform to manage system logs and monitor system health and performance, making it a crucial log management solution for system administrators and network engineers to adopt.
How to configure Syslog Monitoring?
Syslog is a standard protocol used for sending and receiving log messages in a network. It is commonly used to collect and centralize log data from various devices, applications, and systems for monitoring and analysis purposes. Here are the steps to configure Syslog monitoring:
- Identify the Syslog server: The first step is to identify the Syslog server where you want to send the log messages. This can be a physical or virtual server that collects and stores log data.
- Configure the Syslog agent: The next step is to configure the Syslog agent on the device or application that you want to monitor. Again, Motadata helps you with an agent who will send the log messages to the Syslog server. The configuration process may vary depending on the device or application but typically involves specifying the IP address or hostname of the Syslog server and the port number to use.
- Define Syslog message formats: Syslog messages can be sent in different formats, such as RFC3164 or RFC5424. You should choose a format that is compatible with your Syslog server and provides the necessary level of detail for monitoring and analysis. In addition, you can configure the tags and colors from the Syslog messages to identify the severity and cruciality of the event. Tag management helps you make the prioritized decisions and resolve issues quickly.
Syslog Severity AIOps Severity 0 Emergency 1 Alert 2 Critical 3 Error 4 Warning 5 Notice 6 Informational 7 Debug 8 Trace - Set up filtering and alerting rules: Once the Syslog messages are sent to the Syslog server, you can set up filtering and alerting regulations to notify you of important events or issues. For example, you may want to receive an alert if a critical system error is logged or if a user attempts to access a restricted resource.
- Monitor and analyze Syslog data: Finally, you can use Motadata to view and analyze the log data collected by the Syslog server. This can help you identify trends, troubleshoot issues, and optimize system performance.
Overall, configuring Syslog monitoring requires careful planning and coordination between the Syslog server and the devices and applications you want to monitor. However, with the proper setup, you can gain valuable insights into your network and improve your overall security posture.
Benefits of Syslog Monitoring
The intricacy of present-day applications and frameworks is truly expanding. To comprehend the conduct of intricate frameworks, directors/designers/Ops frequently need to gather and screen all crucial data created by their applications.
Furthermore, such data should be regularly investigated and corresponded to decide how their frameworks are acting. Thus, heads can apply logical information strategies to analyze underlying drivers once issues happen or gain knowledge into flow framework conduct dependent on factual examination.
As often as possible, logs have been applied as an essential and solid information source to satisfy such a mission for loads of benefits, some of which are recorded here:
Troubleshooting
The Syslog monitoring tool allows administrators to identify and troubleshoot issues within a system quickly. By capturing and analyzing Syslog messages, administrators can identify the root cause of problems and take corrective action before impacting system availability or performance.
For example, if there are multiple network devices on the network generating similar log messages, there can be a problem with a shared component or configuration.
Security
Syslog messages often contain important security-related information, such as failed login attempts, system breaches, and malware infections. By monitoring Syslog messages, administrators can detect and respond to security threats in real-time and take steps to prevent future attacks.
For example, suppose any device in the network is trying to access unauthorized resources. In that case, Syslog monitoring can detect this activity and notify the network administrator to take action on the same.
Compliance
Many industries and regulatory bodies require organizations to maintain detailed logs of system activity and to review these logs for compliance purposes regularly. Syslog monitoring provides a centralized mechanism for collecting and analyzing logs, making it easier for organizations to comply with regulatory requirements.
Regulatory compliances such as HIPPA and PCI DSS come with specific requirements for collecting, storing, and analyzing log messages as they help ensure the security and integrity of systems and networks.
Performance
Syslog monitoring can also be used to track system performance and activity over time, allowing administrators to identify bottlenecks, optimize system performance, and plan for future capacity needs.
The performance metrics help you understand the bottlenecks and the reasons for issues. Then, as the admins resolve them, you can get efficient network performance and enhance overall productivity as well.
Complete Visibility
Syslog monitoring can be a valuable tool to get insights into distributed systems, where logs from multiple systems must be collected and correlated to identify the root cause of issues. This provides complete visibility across the IT stack and helps you make confident decisions.
For example, with Syslog Monitoring in practice, network admins can identify the devices that are causing the network issues or generating a high volume of log messages. This helps network admins identify the patterns, such as a sudden increase in traffic, a spike in errors, etc.
Overall, Syslog monitoring is an essential tool for ensuring the health, security, compliance, and performance of IT systems and is an important component of any comprehensive network and system management strategy.
Get Actionable Insights from log data
With Log Analytics
Syslog Monitoring with Motadata AIOps
Log Analytics by Motadata AIOps is a monitoring solution that helps you gather, store and analyze log data collected from various resources such as network devices, servers, and applications. Here are some of the critical features of Motadata AIOps while practicing Syslog monitoring:
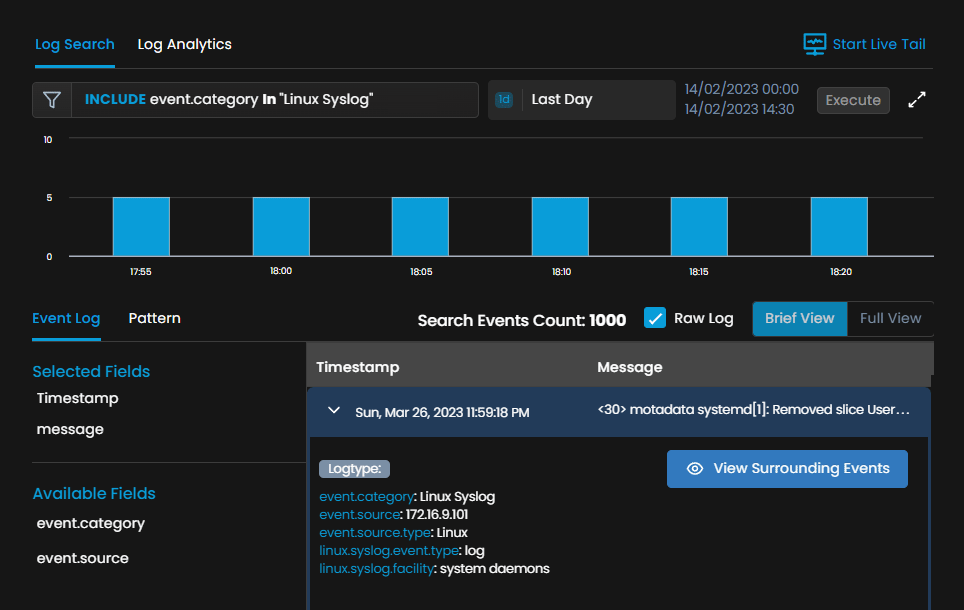
Centralized Logging: It comes with a unified console, a centralized platform where you can access all the log data collected from network elements across your architecture. It is easy to access and provides complete visibility across your IT stack.
Live Log Tails: It provides live log tails in the form of information that can be helpful for network administrators. You can even filter out the events based on activities or the strings to highlight from the live log tails.
Monitor the changes of multiple log sources at once, and the filtering helps you focus on what matters the most and saves you from drowning in an overload of data with a Syslog Management tool. Here are a bunch of benefits you can have with Live Log Tails.
- Real-time Visibility: Get real-time visibility into what’s happening in your system.
- Improved Troubleshooting: Identify and resolve issues quickly, minimizing the downtime and improving overall performance.
- Enhanced Security: Detect security threats in real-time and set up alerts to prevent data breaches.
- Capacity Planning: Discover trends and patterns to plan future investments and optimize resource utilization.
- Compliance: Monitor and retain log data for any specific time to meet regulatory compliance.
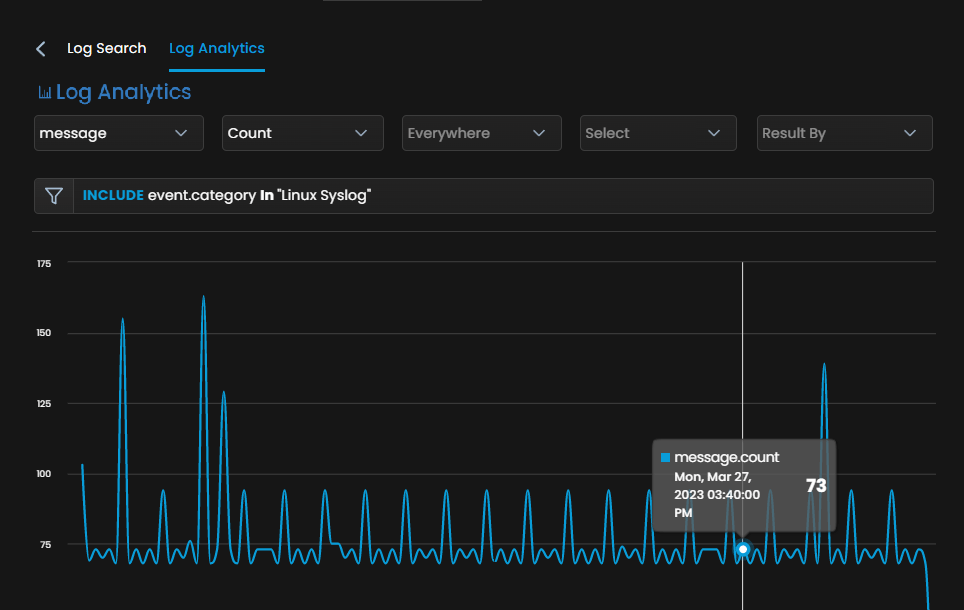
Discover Anomalies & Forecasting: It also comes with the capability of discovering anomalies without human intervention. With the help of different methods, it analyses log data and identifies unusual or abnormal behavior/entries. This helps proactively find the concerns and resolve them before they become inevitable problems. Here are the benefits one can obtain while discovering anomalies and forecasting.
- Early stage Detection: Detect abnormal behavior, sudden changes, or error rates at an early stage to prevent potential damage.
- Proactive Approach: The proactive approach lets you take proactive measures to prevent issues from occurring.
- Reduced Downtime: Early detection lets you reduce downtime and deliver better services.
- Improved Performance: Optimized performance improves resource utilization and saves overall cost and time.
Reports & Dashboards: Get out-of-the-box reports on demand to get complete visibility into network operations. Detailed, customized, and actionable dashboards help prevent potential incidents. It also allows administrators to make informed decisions and capacity planning. In addition, it can help you meet compliance requirements by providing detailed reports on system activity and user behavior.
With a comprehensive monitoring solution, you can adopt the best Syslog monitoring practices and build robust network infrastructure. As Motadata AIOps is built with AI-ML capabilities, it offers a wide range of monitoring and analytical facilities that ensures seamless network operations and helps you perform network operations efficiently.
In summary, Syslog Network Monitoring with Motadata AIOps lets you add Syslog data sources, create rules, configure notifications, and analyze Syslog data using visualization and reporting tools. With this approach, you can proactively identify and resolve issues before they impact your business operations.