Today, we live in a digital world that faces constant cyber threats, and one missed software update can cause major damage to your data and business goodwill.
Reports state that 32% of cyberattacks begin due to unpatched vulnerabilities, leading to massive data breaches and regulatory fines.
Still, most businesses view patch management as a technical maintenance task and underestimate its broader business impact. Unpatched software doesn’t just threaten your security posture; it represents a measurable failure to meet compliance obligations.
Keeping your systems up to date with patches is no longer optional but a necessity. Without it, you can’t maintain compliance across a wide range of industry regulations and security frameworks like GDPR, HIPAA, or PCI DSS. Patching is one of the first step every organization must take to stay compliant and avoid penalties.
It surely comes with certain challenges but still, it is necessary to keep your data and systems protected from threats and known vulnerabilities.
Let’s understand how patching connects directly with legal and regulatory obligations. Further, why every IT Manager, security manager, or IT Operations Leader must treat it as a strategic compliance priority, not just a technical routine.
Understanding the Compliance Landscape: Why Patching Matters More Than Ever
Government and industry regulations have become important to maintain order and safety.
No doubt, we are growing in terms of technology and business but at the same time cybercriminals are adapting new practices to misuse or hamper sensitive and regulated data.
Hence, it has become essential for companies to maintain regulatory compliance in IT.
Also, regulatory bodies must respond with stricter mandates and regulations to ensure businesses operate in a fair manner and are held accountable for cybersecurity.
Some of the mandates that organizations face today include Personally Identifiable Information (PII) and Protected Health Information (PHI) to financial records and intellectual property, GDPR, CCPA for Data Privacy, Security Frameworks like ISO 27001/NIST, etc. Also, industry-specific regulations are available, i.e., HIPAA for healthcare and PCI DSS for payments.
These rules usually expect companies to protect their systems from known security threats, like software bugs or vulnerabilities that hackers could exploit. Secondly, keep their systems stable and running smoothly so important data and services are always available and accurate.
Also, keep clear records showing what steps they’ve taken to stay secure — this helps prove they’re following the rules if they ever get audited.
Non-compliance companies can cost more than just regulatory fines. It can lead to operational outages, damaged customer relationships, legal penalties, and increased scrutiny from boards and stakeholders.
Remember, patch management failures are often cited in post-incident investigations and audit reports – a red flag that due diligence was not followed.
Hence, it is best to invest in automated patch management solutions like Motadata, Manageengine patch manager, solarwinds patch manager, or other options available in the market.
Read Also: ManageEngine vs SolarWinds: An Objective Look at Observability Platforms
Connecting the Dots: How Effective Patching Directly Enables Compliance
A. Closing Known Vulnerability Gaps:
Security standards and regulations demand that organizations address known vulnerabilities in real time. Applying security patches or software updates is the primary response.
But Patch Management for Compliance is seen as negligence. If your organization doesn’t patch a known vulnerability and an incident occurs, regulators will see this as a failure to act on known risks.
This is a direct compliance violation under frameworks like PCI DSS. It can result in penalties, legal issues, or a failed audit.
B. Safeguarding Sensitive Data:
Attackers often exploit unpatched systems to gain unauthorized access to sensitive data. These breaches include access to databases, ERP platforms, email servers.
To avoid this, several regulations like GDPR, HIPAA, and PCI DSS were issues that focussed on keeping personal and sensitive data safe.
Usually, attackers target these systems as they comprise customer names, credit card numbers, and health records which can be used later for fraudulent practices.
Remember if you don’t patch these systems, you’re leaving the door open to attackers.
Whether it’s a web server, database, or business application, failing to apply security updates can directly lead to data breaches. Patching in such cases can help stay compliant.
C. Ensuring System Integrity and Availability:
Some regulations, especially those related to financial reporting (like SOX) or critical services require systems to be available at all times.
A system crash or data loss caused by an unpatched bug can interrupt business operations and damage your compliance standing. It can even affect your ability to report accurately and that’s a compliance problem.
Patches not only fix security vulnerabilities but also improve system performance and stability. They often fix software bugs, compatibility problems, and stability issues that could cause your systems to slow down or fail entirely.
For example, imagine a hospital’s patient data system crashes because of a software flaw that had a patch available for months—but was never installed.
Not only could this impact patient care, but it could also lead to violations of HIPAA regulations.
However, if the patch was installed, you could have prevented downtime, reduce the risk of data loss, and ensure that your systems function as required.
D. Providing Auditable Proof of Due Diligence:
Most regulatory audits look for proof that security measures are in place and that they are followed consistently.
A strong patch management process includes logs and records that show what was patched, when it was done, and by whom.
These records are powerful evidence of your organization’s commitment to cybersecurity and risk management.
If a regulator asks, “How do you protect your systems from known threats?” you need more than a verbal answer. You need logs, reports, and audit trails that show your patching activity over time.
Having detailed patching documentation can be the difference between passing or failing a compliance audit.
Remember, in high-stakes industries such as finance, healthcare, or government, the absence of these records can lead to serious consequences. Having them, on the other hand, offers visibility and security.
Patch Management Across Key Regulatory Areas (Illustrative Examples)
The patching process is not all about running a good security practice. It is more of a requirement under major laws and industry standards incorporated to protect systems, data, and business operations from threats.
Security vulnerabilities are common in organizations, but you can prevent them by implementing an effective patch management system that plays a key role in meeting different regulatory and compliance obligations.
- Data Privacy (e.g., GDPR, CCPA): Laws like the General Data Protection Regulation (GDPR) and the CCPA focus on protecting personal data. These laws require organizations to ensure the “security of processing,” which means keeping the systems that handle personal information secure and protected. If servers, databases, or applications that store personal data aren’t patched, they can become easy targets for attackers. However, with timely patching, you can reduce the risk of unauthorized access and data theft.
- Payment Card Industry (PCI DSS): PCI DSS is applicable to businesses that handle credit card payments. Requirement 6 of PCI DSS specifically states that companies must install security patches quickly to reduce vulnerabilities in systems that store or process cardholder data. For example, a retail store where customer swipes their cards to make payments. Remember, failing to patch in time could lead to breaches and loss of payment processing benefits.
- Financial regulations, such as SOX, serve to safeguard the accuracy and integrity of financial reporting. If critical systems that generate financial reports crash, are corrupted, or are tampered with due to unpatched vulnerabilities, the company could face regulatory scrutiny.
- General Security Frameworks (e.g., ISO 27001, NIST CSF): Standards like ISO 27001 and the NIST Cybersecurity Framework outline best practices for security teams managing cybersecurity risks. Organizations using these standards are expected to patch systems promptly to reduce risk and prove they’re managing threats responsibly.
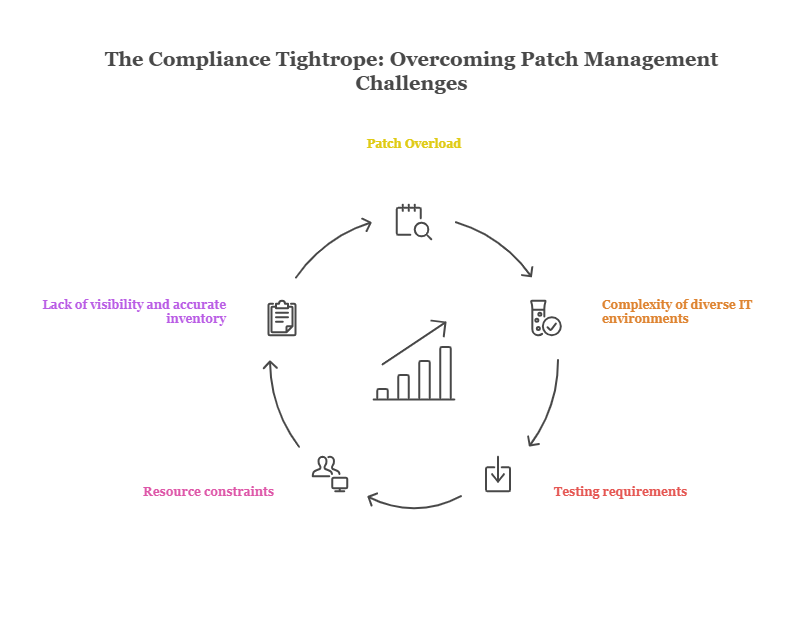
The Compliance Tightrope: Overcoming Patch Management Challenges
Patch management for compliance is not as easy as it sounds. Many businesses find it difficult to keep up with the technical and operational challenges that come with patch management systems.
Here are a few common hurdles that make compliant patching difficult:
- Patch Overload: New patches are released all the time, often in large numbers. For example, Microsoft’s “patch tuesday” releases dozens of security updates at once. Keeping up with this constant stream is overwhelming, especially when each patch needs to be tested and deployed carefully.
- Complexity of diverse IT environments: Devices and applications work in various environments, including operating systems, cloud platforms, and on-premises infrastructure. There can be cases where certain patches work for one system but break another. Managing all these patches in different IT environments can be complicated and challenging.
- Testing requirements: Testing patches before deployment is another challenge. Let’s say the patch was not tested for some reason. As a result, if there is some fault, it could cause software to malfunction or systems to crash. Also, testing patches is a time-consuming process and requires resources.
- Resource constraints: Many IT departments operate with small teams that manage multiple responsibilities. Without enough people or time, patching often gets pushed to the bottom of the list, even if it is crucial for compliance.
- Lack of visibility and accurate inventory: You can’t patch what you don’t know you have. Many organizations lack an up-to-date inventory of their systems, which makes it hard to know which devices are missing patches or are exposed to vulnerabilities.
These minor to major issues make it difficult to meet compliance requirements. If patches aren’t applied in a timely, organized way, it’s not just a technical failure but can compromise security.
Hence, to avoid big problems, it is important to adopt best practices and the right tools to properly manage the patch management process.
Building a Defensible, Compliant Patch Management Program (Best Practices)
Patch management is a structured program designed to meet strict security and compliance requirements. It is no longer limited to fixing bugs or installing updates.
Here are a few best practices that organizations must implement to build a patch management system that not only protects your organization but also keeps you in line with regulatory expectations.
- Comprehensive Asset Inventory: You can’t patch what you don’t know exists. That’s why the first step is to make a full list of every device, system, and software your organization uses.
- Continuous Vulnerability Scanning: Once you have the asset list, you need to scan these systems regularly for missing patches and security weaknesses. Continuous scanning can help find issues early and prevent threats.
- Risk-Based Prioritization: Not all patches are equally urgent. Some fix minor issues, while others protect against serious threats. Focus on patching the most critical vulnerabilities first, especially those that could impact sensitive data.
- Rigorous Testing: Before rolling out patches across your entire network, test them in a controlled environment to avoid system crashes or other compatibility problems.
- Scheduled & Automated Deployment: Set a regular patching schedule and automate as much of the process as possible. Automation saves time, reduces errors, and ensures updates don’t get missed.
- Verification & Reporting: After patches are deployed, check that they were successfully installed. Keep detailed records related to when patches were applied, by whom, and on which systems. It can be used for audits and checking if the company meets security patching regulations.
- Defined Policy & Regular Review: Document the entire process in a formal patch management policy. Review and update it regularly to stay aligned with new risks and compliance requirements.
Leveraging Technology: The Role of Automation & Tools
Certain companies have thousands of devices, servers, and applications across different environments, including on-premises networks, cloud services, and remote work setups.
Tracking, testing, and installing each patch manually can be challenging and time-consuming. Thus, it increases the chances of a serious risk. This is where automation and patch management tools come in together.
Together, the two can help IT managers and experts to keep up with the speed and scale required by modern security and compliance demands.
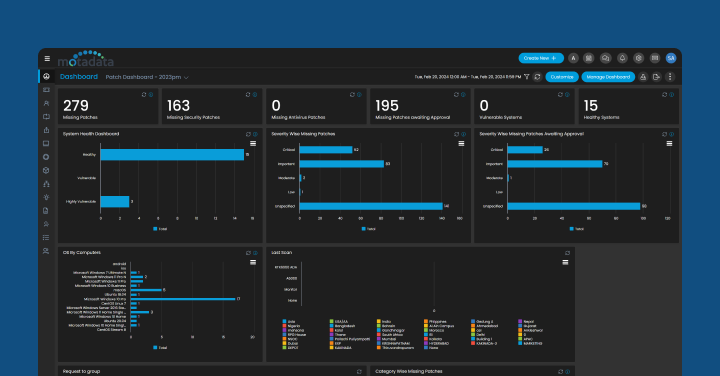
Relying on tools like Motadata’s Patch management software can automate several time-consuming tasks. They can automatically scan all your systems to find out what’s missing or outdated.
Here are a few more benefits of relying on this patch management software:
- Automated Patch Deployment: Automatically downloads, tests, and deploys patches with set schedules. Thus, reducing human errors, saving time, and ensuring consistent updates across different environments.
- Centralized visibility and control: A centralized console is available to monitor all patching activities. You can see which devices are up to date, which need attention, and what risks are associated with each.
- Detailed Reports for Audit: Automatically generate reports that detail the patches applied, their timing, and the individuals responsible. These reports are frequently utilized during audits to demonstrate the organization’s commitment to cybersecurity and compliance with regulatory requirements.
- Helping prioritize based on vulnerability severity: Good patch management software can prioritize updates based on how severe the vulnerability is and how critical the affected system is to your business. Thus, helping fix the risky issues first, improving both security and compliance.
Conclusion: Patching – From IT Chore to Compliance Cornerstone
Patch management is a critical part of maintaining compliance. Regulations across industries are becoming more demanding, and many of them specifically require organizations to protect systems from known vulnerabilities and security risks.
This means patching is not optional but a necessity. If you think installing updates from time to time is patching, you are wrong.
Effective patch management is about more than simply applying updates. It requires a well-organized, documented process that includes identifying which assets need patching, understanding which vulnerabilities are the most critical, testing patches properly, and ensuring successful deployment.
Just as important, it involves keeping detailed records of every step taken. These records are what regulators and auditors look for to confirm that your organization is fulfilling its security responsibilities.
Remember, unpatched vulnerabilities are one of the most common ways attackers gain access to systems.
By patching regularly and on time, you significantly lower the chances of a security breach that could lead to data loss, financial penalties, and reputational damage.
It also strengthens your ability to protect sensitive information like customer data, health records, or payment details, helping you stay aligned with regulations like GDPR, HIPAA, and PCI DSS.
Organizations are far better prepared to survive audits and meet compliance goals when they treat patching as a strategic function, not just a technical task.
If your organization wants to take patch management to the next level, automation and smart tools can make the process easier. Send your request for a demo session to see automated patching and compliance reporting in action.