Understanding Ransomware Attack
The news about Wannacry Ransomware attacks has been doing rounds everywhere – be it over the social media, news or even your messaging apps.
So what is it exactly? What are these attacks all about?
Let’s give you a quick run-through over these nasty ransomwares –
As the name suggests “Ransomware” – Ransom + Malware.
It is a type of computer malware which encrypts disks, files and eventually locks computers. The attacker/hacker then demands a ransom for the decryption tool which has to be paid within a time frame.
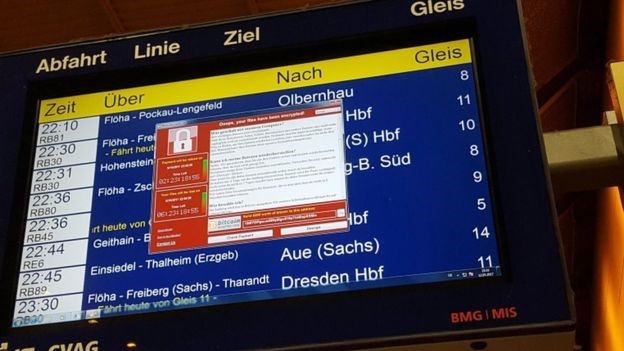
Victims of the attack are confronted with a pop-up window which tells them that their files are now encrypted/locked and now they need to send $300 via the bitcoin cryptocurrency.
“You can decrypt some of your files for free,” reads the message, which we’re seeing today in a variety of languages. “But if you want to decrypt all your files, you need to pay. You only have 3 days to submit the payment. After that the price will be doubled.”
One of the simplest ways for hackers could be – to check up on victim’s social media accounts and also create a fake mail address pretending to be a friend or a common contact in order to get the victim to click on the infected attachment or link.
Education, health and transportation sector is said to be highly targeted but no sector seems to be untouched by the fear of being attacked.
As per the annual report published by a security team from SonicWall, their Global Response Intelligence Grid saw around 3.8 million ransomware attacks attempted in 2015. Which was a modest rise from the 3.2 million tallied in 2014, around 19%.
Ransomware attacks have been growing at a blistering pace. In total, SonicWall reports 638 million. That’s more than 167 times the number of attacks in 2015.
Beyond the staggering volume of the attacks, there are the huge sums of money that individuals and organizations paid to (hopefully) get their files decrypted. Though it’s difficult to give a truly accurate total — not everyone hit by ransomware is keen to talk about such incidents — SonicWall’s report estimates that around $209 million in ransoms were paid in the first quarter of 2016 alone.
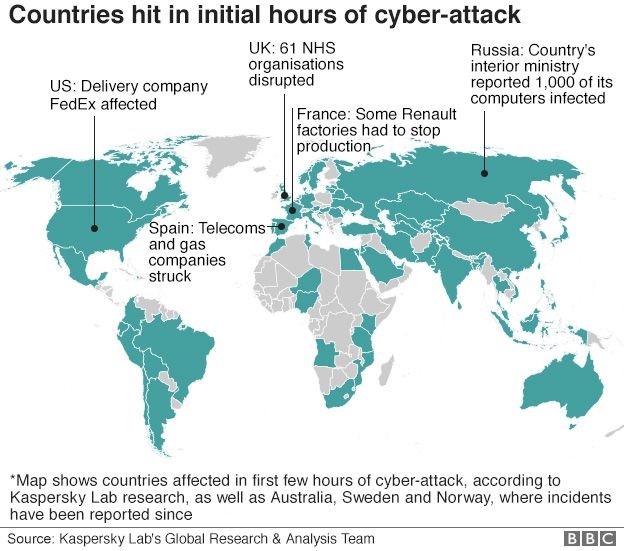
Now in 2017, the first infections were reported at around afternoon UK time on 12th of May 2017 (Friday). First, there were reports of Spain’s largest telecom being hit with pop-up windows demanding a $300 ransom to access files. Then at least 16 hospitals in England’s National Health Service were affected, locking doctors and nurses out of patients’ records unless they paid up. The first of these attacks on networks around the world were reported on Friday.
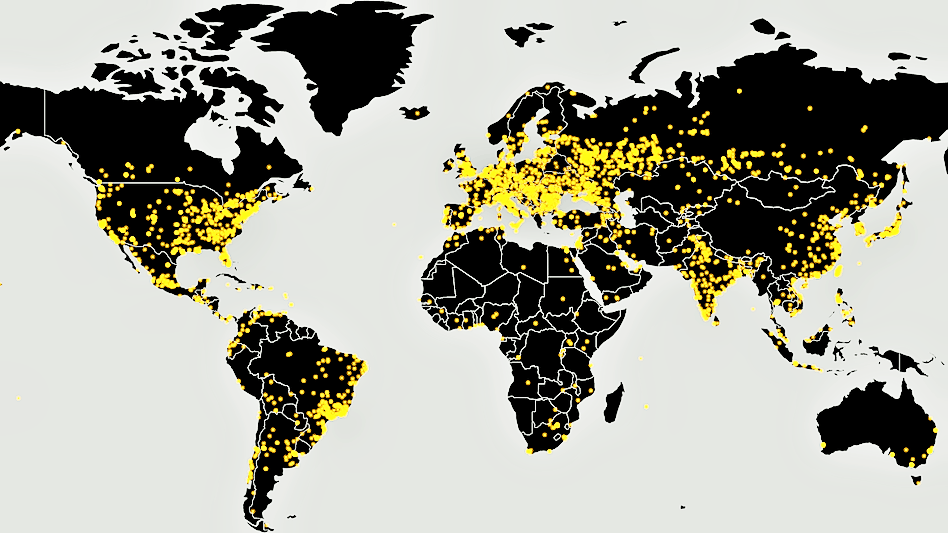
“Currently, we have recorded more than 45,000 attacks of the WannaCry ransomware in 74 countries around the world, mostly in Russia,” cyber security firm Kaspersky says. We’ll note that Kaspersky supports NPR and is a provider of security services for its IT systems.
Friday’s attacks are being blamed on a piece of malware called WannaCry, WCry, WanaCrypt and WanaCrypt0r – encrypted files extension are changed to .wnry, .wcry, .wncry and .wncrypt, that’s been tracked in large-scale attacks in Europe and Asia — particularly Russia and China — and a scattering of attacks in the U.S. and South America. (Source: Malware Tech)
Wannacry Decryptor 2.0 ransomware is now the fastest malicious ransomware.
What should be blamed? Antiquated or misconfigured security systems? Or loosely held/ unprotected sensitive data assets?
The blame-game won’t really help, since the attackers have now caught the hold of massive valuable assets.
These attacks usually exploit a specific vulnerability in a server, application, device or a software.
The impact of these attacks influences both the levels – Individual/user level and company/organization level.
Victims around the globe (2017)
- NHS, UK – Healthcare Industry
- Telefonica, Spain – Telecommunication Industry
- FedEx,USA – Multinational Courier Delivery Services
- University of Waterloo, USA – Educational Sector
- Сбера bank, Russia – Banking Sector
- Portugal Telecom – Telecommunication Industry
- Russian and German Railways & many more!
“Activity from this ransomware family was almost inexistent prior to today’s sudden explosion when the number of victims skyrocketed in a few hours,” Bleeping Computer’s Catalin Cimpanu states.
In the U.S., the Computer Emergency Readiness Team, or CERT, says it has “received multiple reports of ransomware infections in several countries around the world,” without identifying those countries.
These attacks have got its roots into vulnerabilities and the best way out is to safeguard all your assets.
Defeating Ransomware
So investing in an effective preventive measure sounds like a saviour to us!
In the greatest hour of the need NMS & SIEM tools on the plate might prove to be useful.
Some of the known Indicators of Compromise file name also referred to as IOCs
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Some of the known Command and Control servers also referred to as CnC servers
- 188.166.23.127:443
- 193.23.244.244:443
- 2.3.69.209:9001
- 146.0.32.144:9001
- 50.7.161.218:9001
- 217.79.179.77
- 128.31.0.39
- 213.61.66.116
- 212.47.232.237
- 81.30.158.223
- 79.172.193.32
- 89.45.235.21
- 38.229.72.16
- 188.138.33.220
Few attackers’ domains identified
- gx7ekbenv2riucmf(.)onion
- 57g7spgrzlojinas(.)onion
- xxlvbrloxvriy2c5(.)onion
- 76jdd2ir2embyv47(.)onion
- cwwnhwhlz52maqm7(.)onion
- sqjolphimrr7jqw6(.)onion
- hxxp://iuqerfsodp9ifjaposdfjhgosurijfaewr wergwea(.)com
- easysupport.us
- fkksjobnn43.org
- trialinsider.com
- ecoland.pro
- holdingair.top
- palindromus.top
- serionbrasil.com.br
Known URLs
- http://146.0.32.144:9001
- http://188.166.23.127:443
- http://193.23.244.244:443
- http://2.3.69.209:9001
- http://50.7.161.218:9001
List of file extensions
der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .sxw, .stw, .3ds, .max, .3dm, .ods, .sxc, .stc, .dif, .slk, .wb2, .odp, .sxd, .std, .sxm, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .mdf, .ldf, .cpp, .pas, .asm, .cmd, .bat, .vbs, .sch, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .mkv, .flv, .wma, .mid, .m3u, .m4u, .svg, .psd, .tiff, .tif, .raw, .gif, .png, .bmp, .jpg, .jpeg, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .ARC, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .dwg, .pdf, .wk1, .wks, .rtf, .csv, .txt, .msg, .pst, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotm, .dot, .docm, .docx, .doc.
How an effective networking monitoring & SIEM tools can help?
- Network Monitoring
- Setting up alerts and blocking communication with malicious IP addresses/CNC servers, URLs, domains, and suspicious geographic destinations
- Allowing pre-mentioned IP addresses for file access
- Network Monitoring of firewall, switch etc.
- Network Traffic/Flow Monitoring
- Comparing and correlating traffic volume against baseline number
- Https and Http monitoring for safeguarding from suspicious URLs mentioned above
- Log Management/SIEM – Behavioural analysis by monitoring logs of all devices including operating systems
- Increased number of administrator’s logins from both admin & non-admin computers
- Log management to check for IOCs and CNC servers
- Log monitoring for suspicious log entries including unauthorized software setup
- Soaring number of endemic modifications in the file system (file names and contents changes, files deletion) which is part of maintaining file Integrity
- Instant alert for security breach
Few more preventive measures at an organizational and user level include:
- Do not click on hyperlinks from un-known sources, and without establishing the authenticity of the link even from known sources.
- Prepare an up-to-date inventory of all the “Digital Assets” at various locations/facilities being used by the various functionaries of the organization. SIEM tools also maintain file integrity of your valuable assets. With the use of a good SIEM tool you can also track who is accessing your confidential data and at the same time block the unauthorized user.
- Back up all digital content to a secure, offsite secret location(s) within organization.
- Distribute Back-up: Divide the digital assets and distribute the back-up locations. Don’t place all data on one back-up file and share it.
- Develop a secret communication channel and strategy to quickly inform all employees if a virus reaches the company network.
- Adopt and use standard security and data privacy policies as per advisories from ITE&C Dept. NIC/ Govt. of India.
- Ensure all devices and systems are protected well with latest firewalls and anti-virus systems.
For more information on how Network Monitoring & SIEM tools can help prevent ransomware attacks, contact Motadata team – sales@motadata.com or support@motadata.com.
Discover it yourself – www.motadata.com/download